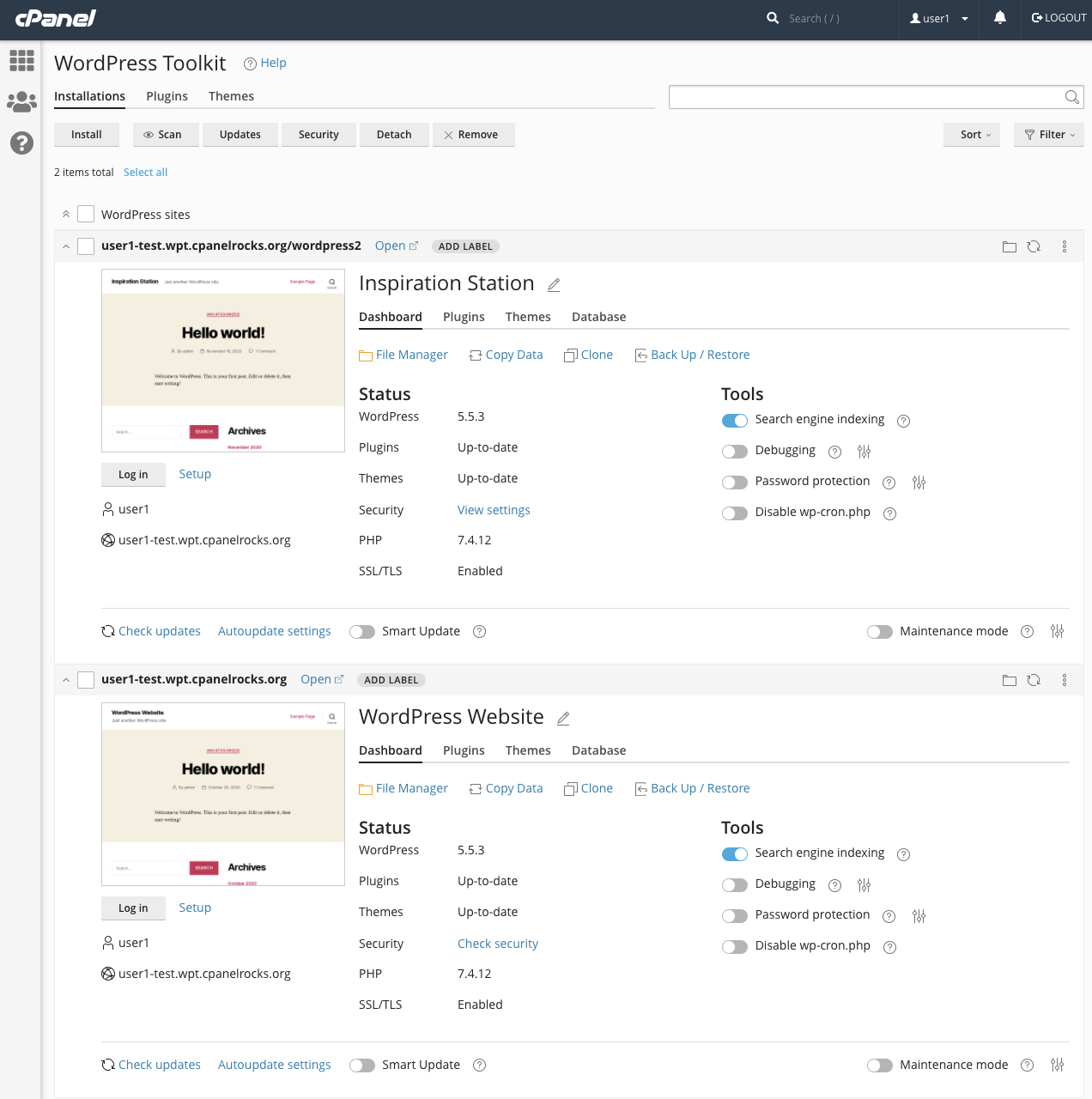
WordPress Hardening: One-Click Security with cPanel | cPanel Blog
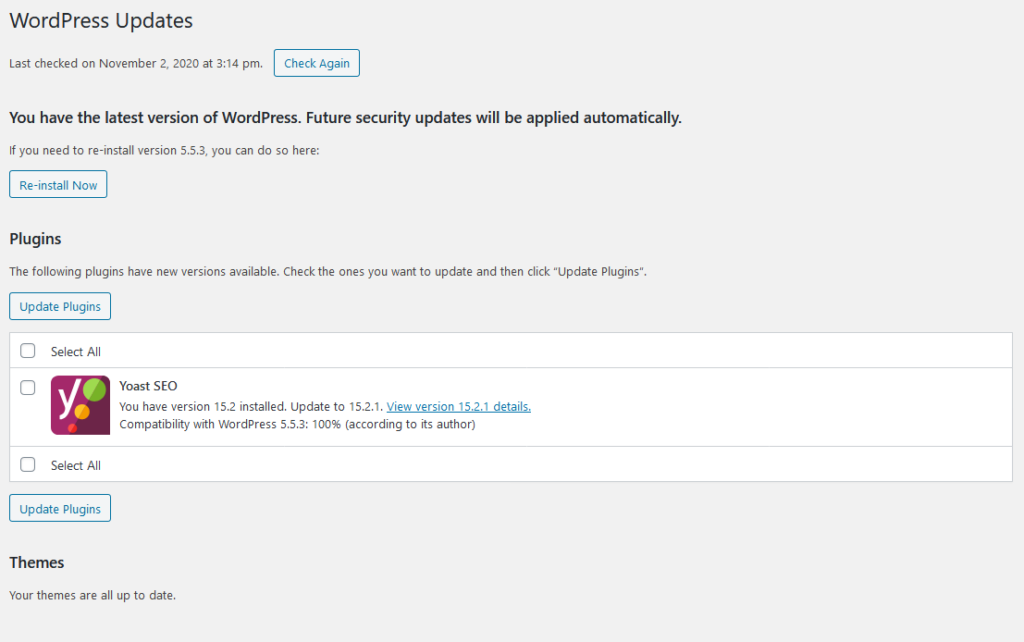
WordPress is far and away the most widely-used content management system on the web, but that popularity comes at a price. It’s also the most attacked CMS. Not because it’s un-secure, but because attackers know that a WordPress vulnerability is a gateway to tens of millions of websites. As soon as a WordPress website goes…


![How to Write, Compile and Run a C Program in Ubuntu and Other Linux Distributions [Beginner’s Tip] how-to-write-compile-and-run-a-c-program-in-ubuntu-and-other-linux-distributions-beginners-tip](https://wiredgorilla.com/wp-content/uploads/2020/11/how-to-write-compile-and-run-a-c-program-in-ubuntu-and-other-linux-distributions-beginners-tip.png)