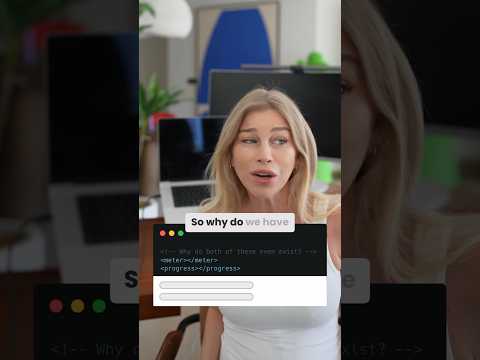
Unlocking the Secrets of Writing Custom Linux Kernel Drivers for Smooth Hardware Integration
Introduction Kernel drivers are the bridge between the Linux operating system and the hardware components of a computer. They play a crucial role in managing and facilitating communication between the OS and various hardware devices, such as network cards, storage devices, and more. Writing custom kernel drivers allows developers to interface with new or proprietary…
Copywriting 101: The Complete Guide to Writing Amazing Marketing Copy | WordStream
Copywriting is a fundamental element of marketing. Your copy appears in your ads, on your website, across your social channels, and more. That’s why it’s so important to have strong, persuasive, and attention-grabbing copy. In this crash course in writing great copy, we’ll cover what copywriting is, what a copywriter does, and how to write…

Australia’s New AI Regulations Aim to Tidy Up the Chaotic Artificial Intelligence Market
The Australian federal government has introduced a proposed set of mandatory guardrails for high-risk artificial intelligence (AI) and a voluntary safety standard for organizations using AI. The guardrails focus on accountability, transparency, record-keeping, and human oversight of AI systems. The proposed requirements for high-risk AI aim to prevent or mitigate potential harms to Australians. The…
AI influencer marketing: Enhancing your campaigns with AI tools
Evolutions in artificial intelligence (AI) technology have impacted the way brands and businesses market to customers. Accessible tools now allow companies to streamline campaign management and create more effective, targeted campaigns. One essential digital strategy that continues to feel this impact is influencer marketing. Marketers are learning how to balance the creativity of influencer campaigns…
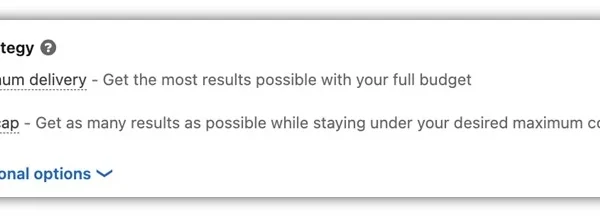
The Complete Guide to LinkedIn Ads Bidding Strategies | WordStream
Just like all of the other major, self-serve advertising platforms out there, LinkedIn has a few different bidding strategies that can help you achieve the performance you want from your campaigns. In this article, I want to walk through the available bidding strategies for LinkedIn ads, talk about how each of them works and how…
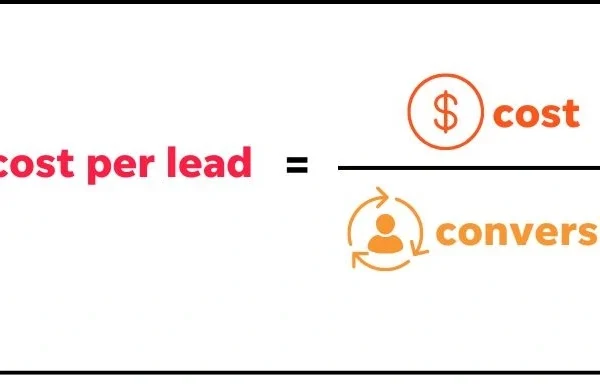
7 Easy Ways to Lower Cost Per Lead Fast | WordStream
Cost per lead (CPL) is a significant metric in digital advertising. For pay-per-click (PPC) and social media campaigns, businesses monitor CPL to understand whether their marketing efforts (and associated costs) are worth it. The more expensive it is to acquire a lead, the less gross profit you’ll expect to see in the long run, as…

Galaxy Watch 7 – Tips Tricks & Hidden Features!!
I have a TON of Tips and Tricks on the Samsung Galaxy Watch 7 that will make it feel SUPER Ultra, and maybe even a bit better!! ? Animated Wallpapershttps://haylsworld.com/collections/callscreens Read moreInstalling and Configuring your OnApp Cloud? Phone Wallpapershttps://haylsworld.com/collections/wallpaper-packs ? Shophttps://haylsworld.com ? SOCIAL ?• SHORTS – https://www.youtube.com/c/HaylsWorldShorts• INSTAGRAM – http://instagram.com/haylsworld• TWITTER – https://twitter.com/HaylsWorld• TIKTOK –…
For when you can’t afford a Cybersecurity Engineer……
Small businesses need to make cybersecurity a priority. Take it seriously TODAY with BitDefender: https://ntck.co/BitdefenderSmallBusiness #bitdefender #cybersecurity #smallbusiness #ad

Welcome new laws addressing technology-based abuse in NSW, but police and courts must also take action.
The New South Wales Premier, Chris Minns, has announced a series of reforms aimed at strengthening legal responses to family violence in the state. These reforms come in the wake of the alleged murder of Molly Ticehurst by her former partner earlier this year. One of the key aspects of the reforms is the revision…

What is DNS? (and how it makes the Internet work)
DNS can be hacked….use SecureDNS from Twingate to protect yourself and your people: https://ntck.co/twingate_zerotrust ? Your Web Browser is Dumb….without DNS?Did you know your web browser is clueless when it comes to finding websites? When you type in a URL like academy.networkchuck.com, your browser has no idea where to go. That’s where DNS, the Domain…

Major review finds no link between mobile phones and brain cancer after 28 years of research
A new systematic review conducted by the World Health Organization has found no link between mobile phone use and brain cancer. The review, published in the journal Environment International, examined over 5,000 studies and concluded that exposure to radio waves from mobile phones and wireless technologies does not increase the risk of brain cancer. This…
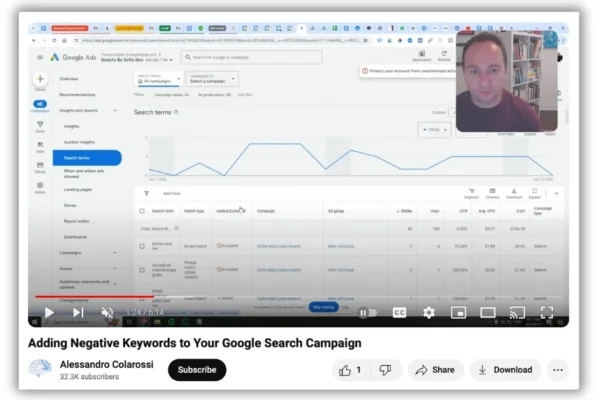
5 Powerful Google Ads Reports to Track Results | WordStream
Running successful Google Ads campaigns requires more than just setting up ads and hoping for the best. To truly optimize your efforts and maximize your return on investment (ROI), you need to leverage the powerful reporting tools that Google Ads offers. These reports provide invaluable insights into various aspects of your campaigns, helping you make…

Locale-sensitive text segmentation in JavaScript with Intl.Segmenter | MDN Blog
Text segmentation is a way to divide text into units like characters, words, and sentences. Let’s say you have the following Japanese text and you’d like to perform a word count: ??????????????? If you’re unfamiliar with Japanese, you might try built-in string methods in your first attempt. For English strings, a rough way to count…

15+ Free Tailwind CSS Number Inputs for your Projects
Tailwind CSS is a popular framework for its utility-first approach, enabling developers to create beautiful, responsive, and highly customizable user interfaces with ease. Number inputs are essential components of any web form, whether you’re building a checkout form, a settings page, or a user profile section. Read moreHow To Choose A WordPress Theme – Free,…

Could other countries follow Brazil’s lead in banning X?
Brazil, the country with the fifth largest number of internet users, has recently banned the social media platform X (formerly known as Twitter). The ban came into effect following a dispute between Elon Musk, the owner of X, and Brazil’s Supreme Court Justice Alexandre de Moraes. De Moraes had previously ordered the platform to block…

IPv6 keeps getting hacked
Take care of your biggest vulnerability — passwords!!: https://dashlane.com/networkchuck50 (50% off) with code NETWORKCHUCK50 Uncover the latest cybersecurity threat with NetworkChuck as we delve into a critical IPv6 flaw affecting all Windows users. Learn how hackers can exploit this vulnerability to gain remote access without any user interaction, and discover practical steps to protect your…