Category: Coding

Azure Lightweight Generative AI Landing Zone – DZone
AI is under the hype now, and some products overuse the AI topic a lot — however, many companies and products are automating their processes using this technology. In the article, we will discover AI products and build an AI landing zone. Let’s look into the top 3 companies that benefit from using AI. Github…

They Sell Your Data to EVERYONE
Data brokers know a lot about us. They silently harvest any information they can find, by purchasing information, using trackers, scraping social media, ingesting data breaches.They compile this information into databases, and sell access so that others can sift through the most private and sensitive areas of our lives. In this video we pull back…

Automate Migration Assessment With XML Linter – DZone
When people think of linting, the first thing that comes to mind is usually static code analysis for programming languages, but rarely for markup languages. In this article, I would like to share how our team developed ZK Client MVVM Linter, an XML linter that automates migration assessment for our new Client MVVM feature in…
Evolution of Top Database Schema Change Tools – DZone
Database schema migration may be the riskiest area in application development – it’s tough, risky, and painful. Database schema migration tools exist to alleviate pain and have come a long way: from the basic CLI tools to GUI tools, from simple SQL GUI clients to the all-in-one collaboration database platform. Command-Line Clients (CLI) – MySQL…

Migrating from JUnit 4 to JUnit 5: A Step-by-Step Guide – DZone
JUnit has been one of the most popular testing frameworks for a long time, with 85% of Java developers claiming to use it in JetBrains’ 2021 survey. In addition, JUnit also plays a crucial role in the practice of TDD (test-driven development), a trending strategy for dev teams all over the world. Developers use JUnit…
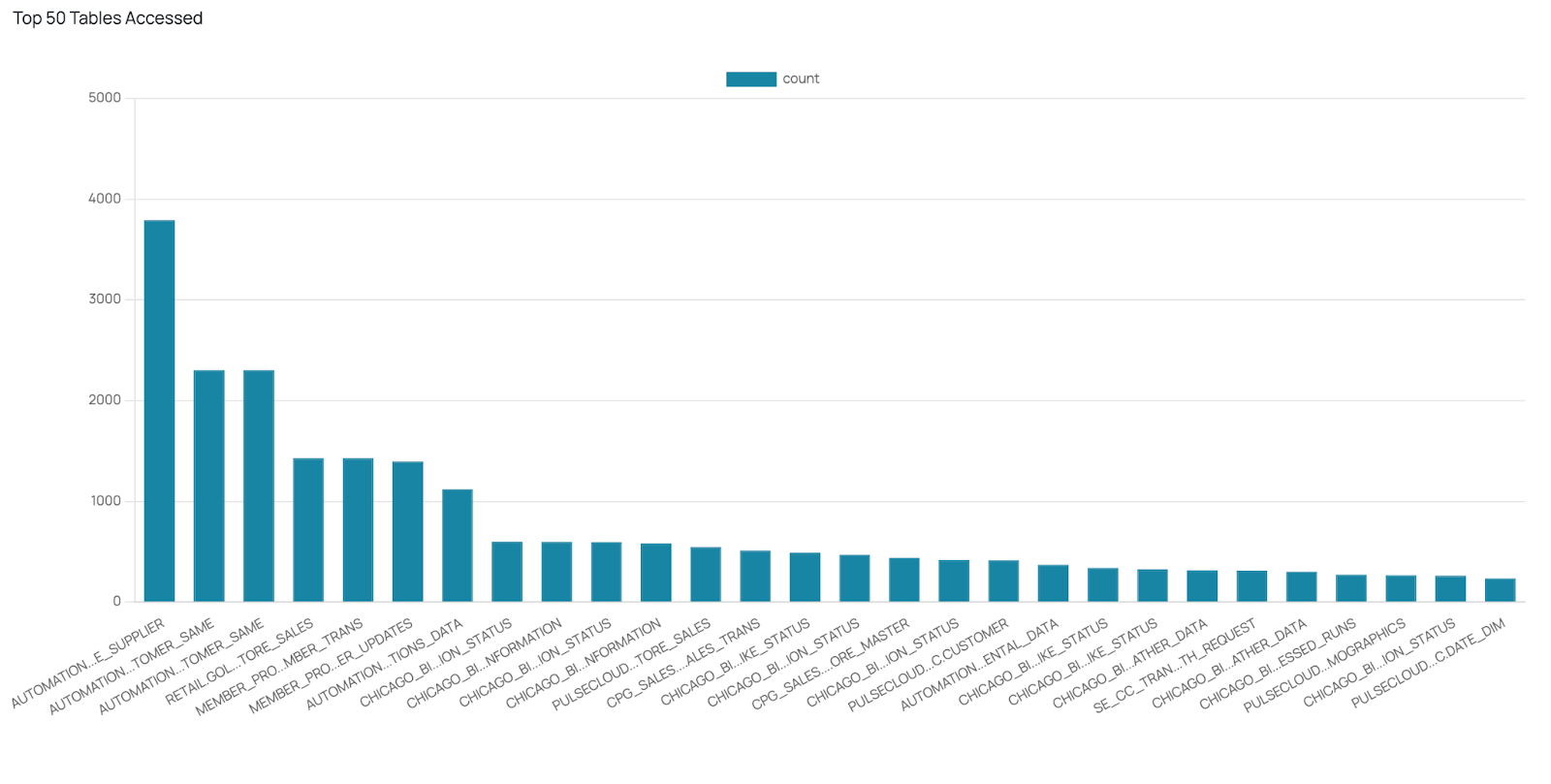
Snowflake Workload Optimization – DZone
In the era of big data, efficient data management and query performance are critical for organizations that want to get the best operational performance from their data investments. Snowflake, a cloud-based data platform, has gained immense popularity for providing enterprises with an efficient way of handling big data tables and reducing complexity in data environments….
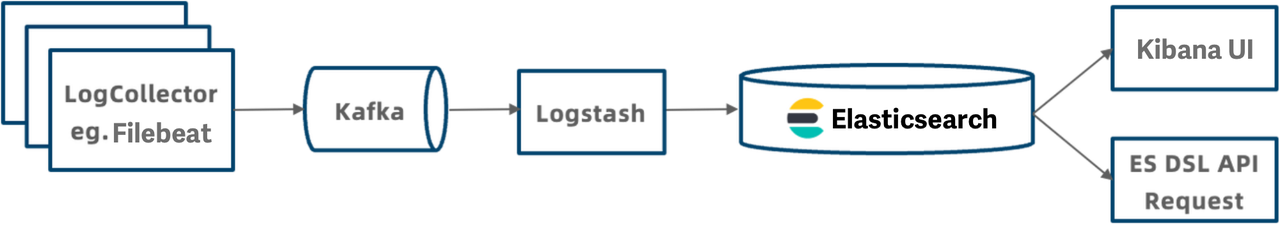
Log Analysis: Elasticsearch vs. Apache Doris – DZone
As a major part of a company’s data asset, logs bring value to businesses in three aspects: system observability, cyber security, and data analysis. They are your first resort for troubleshooting, your reference for improving system security, and your data mine, where you can extract information that points to business growth. Logs are the sequential…

Revolutionizing AI: Unveiling the Power of WatsonX – DZone
In the ever-evolving landscape of artificial intelligence, a new player has emerged to redefine the boundaries of what’s possible. Enter WatsonX, a groundbreaking technology that promises to revolutionize the AI landscape. In this blog post, we’ll dive deep into the intricacies of WatsonX, explore captivating examples, and unveil the potential use cases that can truly…

8 Ways to Improve Application Performance – DZone
Application performance is critical for delivering a fast and responsive user experience. Slow performance, or high latency, can lead to frustrated users and lost revenue for the organization. From a high level, application latency refers to the delay between the user’s request and the application’s response. Latency can not only impact the overall user experience…

How to Create Customer Resource Definitions in Kubernetes – DZone
Kubernetes is a popular open-source platform used for automating the deployment, scaling, and management of containerized applications. It provides a powerful API for managing resources, but sometimes its built-in resources are not sufficient for your use case. That’s where Kubernetes Custom Resource Definitions (CRDs) come in. CRDs allow you to define your own custom resources,…
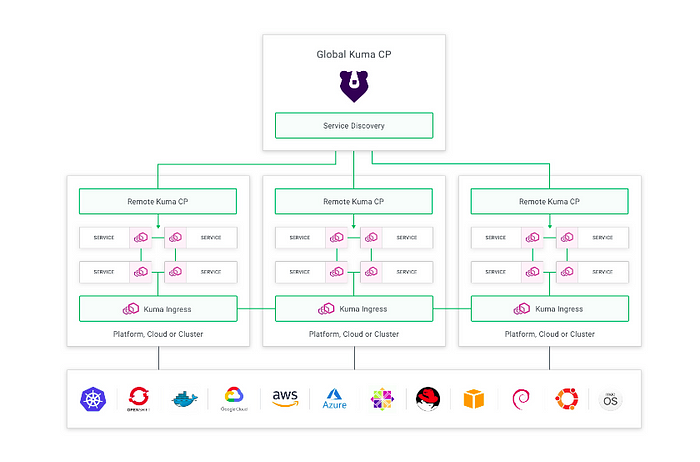
Demystifying Kuma Service Mesh – DZone
Service mesh emerged as a response to the growing popularity of cloud-native environments, microservices architecture, and Kubernetes. It has its roots in the three-tiered model of application architecture. While Kubernetes helped resolve deployment challenges, the communication between microservices remained a source of unreliability. Under a heavy load, the application could break if the traffic routing,…

Things to Consider When Scaling Analytics for High QPS – DZone
For some, the thought of analytics and high QPS (queries per second) together may seem unlikely. After all, we typically think of analytics as the occasional report and dashboard into business metrics. But, analytics use cases are evolving with high volume, low latency queries on the rise. Companies like Confluent, Target, and Pinterest use analytics…

Banks Are SELLING Your Financial Data!
Financial privacy is essential for a free society, because it allows us to support causes we believe in without fear of retribution, to flee dangerous situations without being tracked, to live our daily lives without feeling like every choice we make is on display and needs to be self-censored. How can we have a truly…

Defensive Programming With Klojang Check – DZone
Unit testing and integration testing have long since become established practices. Practically all Java programmers know how to write unit tests with JUnit. IDEs will help you with it and build tools like Maven and Gradle and run them as a matter of course. The same cannot be said of its (sort of) runtime counterpart:…

5 Strategies for Strengthening MQTT Infrastructure Security – DZone
Our previous articles of this series explored various methods to safeguard IoT devices from cyberattacks, including encryption, authentication, and security protocols. However, it is crucial to acknowledge that regular updates and maintenance are equally vital to ensure the ongoing security of IoT devices. Moreover, with the increasing migration of systems and services to the cloud,…
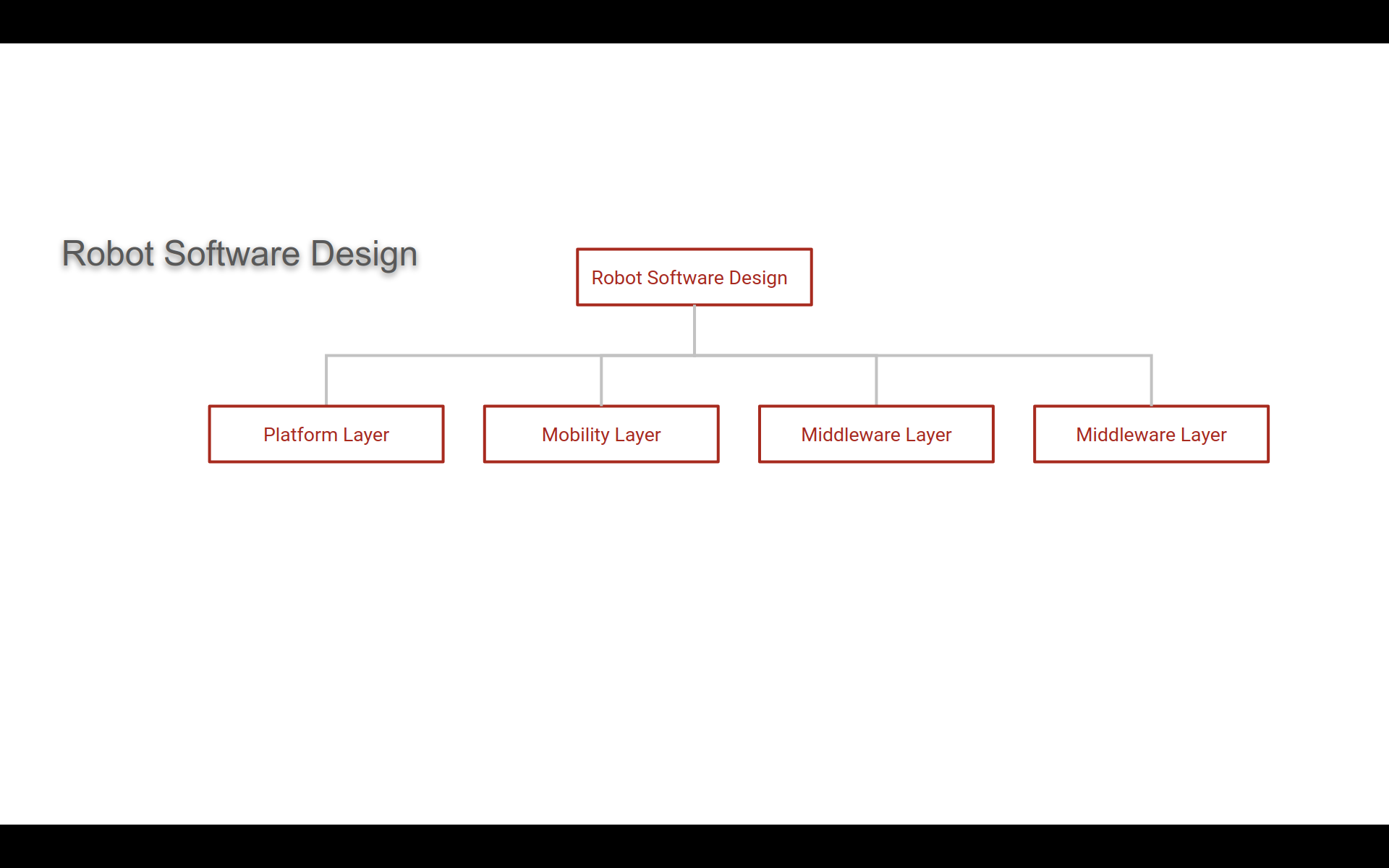
Introduction to Software Testing of Home/Industry Robots – DZone
In this article, I aim to debunk how to approach the testing of robotics software. Robotics involves intricate microprocessors, embedded systems, and diverse software stacks. Software quality engineers play a crucial role in testing these intricate software components to ensure seamless functionality and performance. I will explore the different software stacks utilized in robotics and shed…

Announcing the MDN front-end developer curriculum | MDN Blog
Part of our focus for 2023 is on making MDN a resource where people can learn new skills, as well as becoming familiar with navigating and using reference documentation. Back in 2019, we launched Learn web development on MDN to help folks learn the basics of front-end development. With a lot of useful content published…