Basic SEO for Blogger – Adding Alt Text To Images
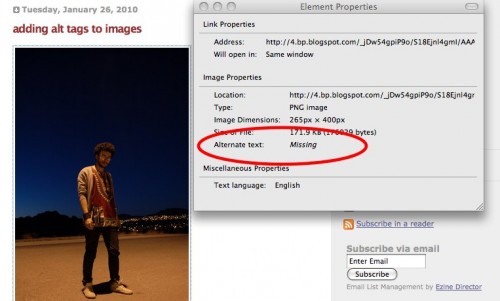 I personally use and am a huge fan of WordPress – I made the switch from Blogger many years ago. However I do have a couple of clients that use blogger to publish their blogs – they find it simpler…
I personally use and am a huge fan of WordPress – I made the switch from Blogger many years ago. However I do have a couple of clients that use blogger to publish their blogs – they find it simpler…


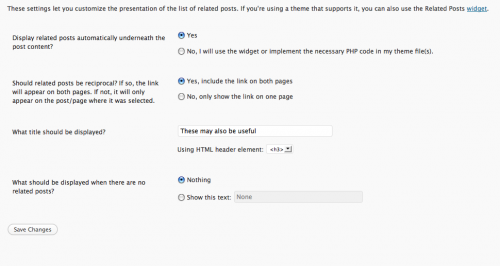 Microkids Related Posts WordPress Plugin Why you need it Related post plugins allow you to present your reader with other content they may find useful or interesting. This helps keep your reader browsing your site and also provides additional internal…
Microkids Related Posts WordPress Plugin Why you need it Related post plugins allow you to present your reader with other content they may find useful or interesting. This helps keep your reader browsing your site and also provides additional internal…  I’ve been attending quite a few different networking events and groups lately, to expand both my business and social circles and so I’ve been thinking about how social networking happens on and offline. For me, networking is about more than…
I’ve been attending quite a few different networking events and groups lately, to expand both my business and social circles and so I’ve been thinking about how social networking happens on and offline. For me, networking is about more than…  A Guide To Online Marketing Terms – Part 2 This is the second part of my developing series on online marketing terms explained. This time we focus on some basic SEO-related terms you might come across. SEO Search Engine Optimization…
A Guide To Online Marketing Terms – Part 2 This is the second part of my developing series on online marketing terms explained. This time we focus on some basic SEO-related terms you might come across. SEO Search Engine Optimization… 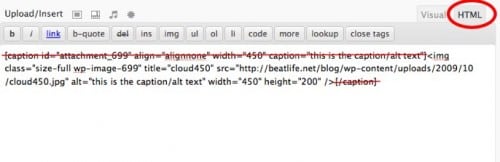 In version 2.6 WordPress introduced the captions feature which meant that when you uploaded an image, the text you entered as the ‘alt’ text, previously only visible to search engines, was now used as a caption under your image, visible…
In version 2.6 WordPress introduced the captions feature which meant that when you uploaded an image, the text you entered as the ‘alt’ text, previously only visible to search engines, was now used as a caption under your image, visible…