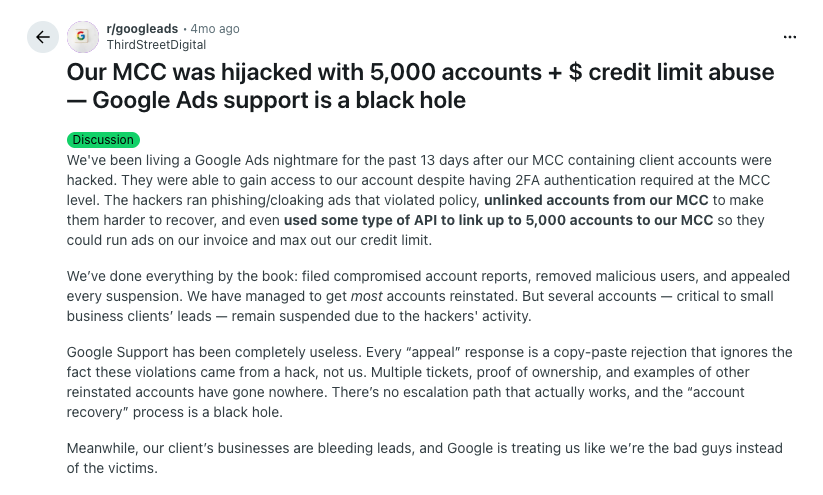
A wave of sophisticated phishing attacks is letting scammers hijack full Google Ads Manager Accounts (MCCs), giving them instant access to hundreds of client accounts — and the ability to spend tens of thousands in hours, undetected.
Driving the news. Agencies across LinkedIn, Reddit and Google’s own forums are reporting an uptick in MCC takeovers, even among teams using two-factor authentication. The attackers’ weapon of choice: near-perfect phishing emails that mimic Google’s account-access invitations.
- Victims say hijackers add fake admin users, link their own MCCs, and begin launching fraudulent, high-budget campaigns.
- In some cases, support tickets take days to escalate while money continues to drain.
- One agency reported “tens of thousands” in ad spend racked up within 24 hours.
How it works. The scams look like normal client-access invites — same branding, same format, same copy — but the link leads to a Google Sites page posing as a Google login screen. Once credentials are entered, attackers gain full MCC access.
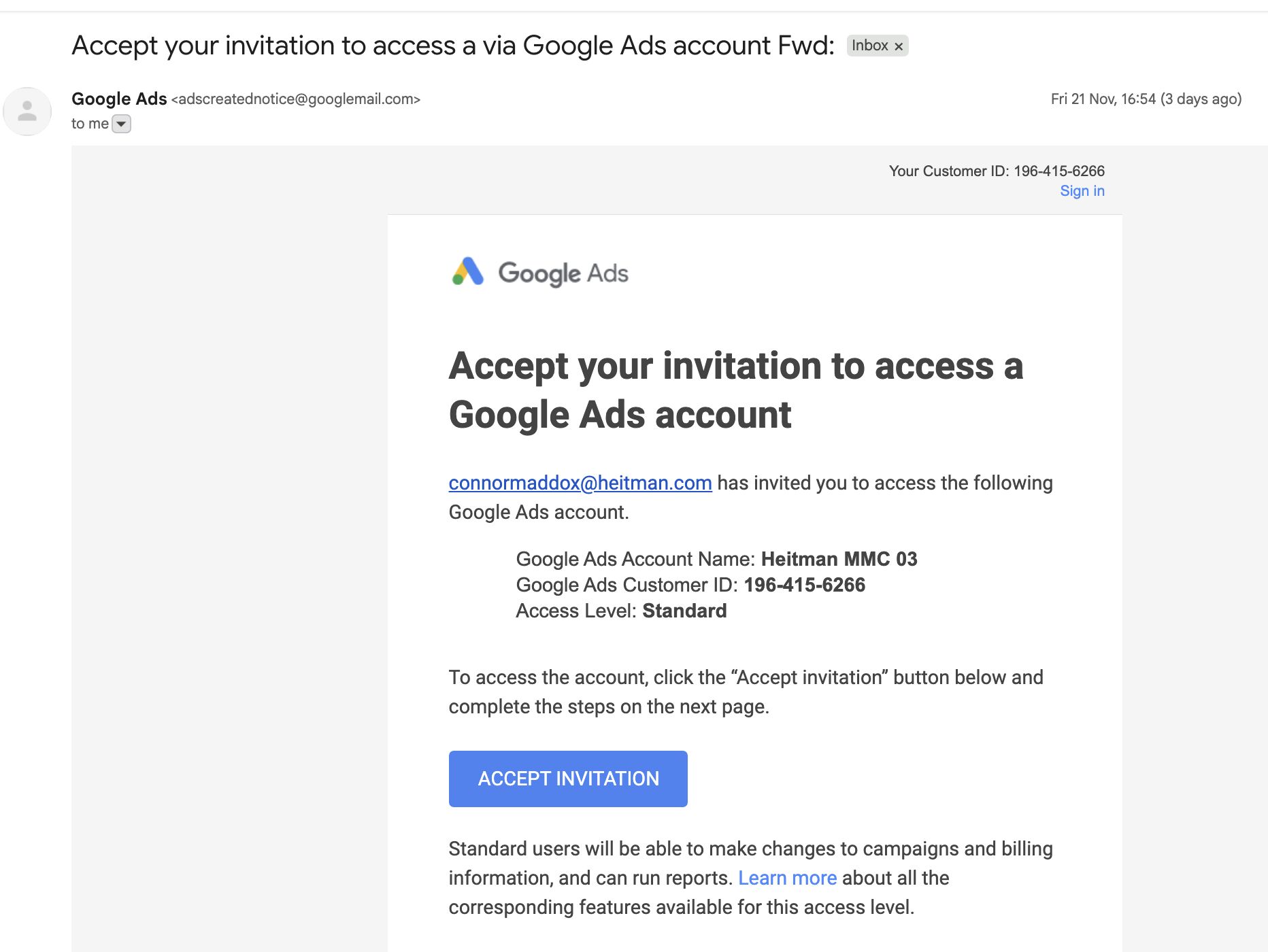
Why it’s getting worse. Advertisers say the phishing attempts are increasingly indistinguishable from legitimate Google messages. Several agencies admitted they would have clicked if not for tiny discrepancies in the sender domain or login URL.
The impact:
- Budgets drained: fraudulent ads run immediately.
- Malware exposure: ads often lead to harmful sites.
- Account damage: invalid activity flags, disapprovals, and trust issues ripple for months.
- Operational chaos: agencies lose access to every client account under the MCC.
What Google says. The Google Ads Community team quietly posted a What to do if your account is compromised help doc, warning advertisers of an uptick in credential theft during the holiday season, but hasn’t acknowledged the scale of the MCC takeover trend.
Why we care. These MCC hijacks aren’t just isolated security issues — they’re direct financial and operational threats that can wipe out budgets, compromise every client account, and take days for Google to contain. With attackers now bypassing 2FA through near-perfect phishing, even well-secured teams are suddenly vulnerable. If just one team member slips, an entire portfolio of accounts — spend, performance, and client trust — is instantly at risk.
What experts recommend. Founder and Managing Director of Low Digital Ltd, Marc Walker gave these recommendations to avoid having your accounts hijacked:
- Always verify the URL — Google never uses Google Sites for login.
- Confirm invites inside the MCC, not just via email.
- Purge dormant users and inactive accounts to reduce attack surfaces.
- Educate teams on phishing red flags — especially during high-volume holiday outreach.
Between the lines. If even one user in a large MCC falls for the scam, the attacker effectively acquires keys to an entire portfolio — and can drain budgets faster than Google’s support system can respond.
The bottom line. Google Ads hijacks are a growing operational threat for agencies and in-house teams. Until Google ships stronger MCC-level protections, vigilance is the only real defense.
Search Engine Land is owned by Semrush. We remain committed to providing high-quality coverage of marketing topics. Unless otherwise noted, this page’s content was written by either an employee or a paid contractor of Semrush Inc.

