You’ve built your clients their dream website. Don’t allow hackers to take it over and turn it into a nightmare. Our “how not to get hacked” guide shows you how…
When hackers start breaking into the security firms that are protecting us from hackers, you know it’s time to take security seriously!
Especially when you consider stats like these:
- There is a hacker attack every 39 seconds.
- 95% of cybersecurity breaches are due to human error.
- 64% of companies have experienced web-based attacks.
- 43% of cyber attacks target small businesses.
Source: Cybint
Yeah…But Not All Hacking is Done Via Websites
True, but here is the thing…
Most security threats are multidimensional.
This means that no matter how much time, money, and effort you invest into building and hosting a website securely, there are many factors that can threaten web security and allow hackers to wreak havoc on your website.
Take a look at this flowchart to see what I mean…
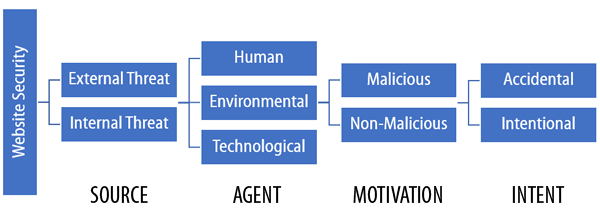
The above is my condensed version of the security threats classification model shown below…
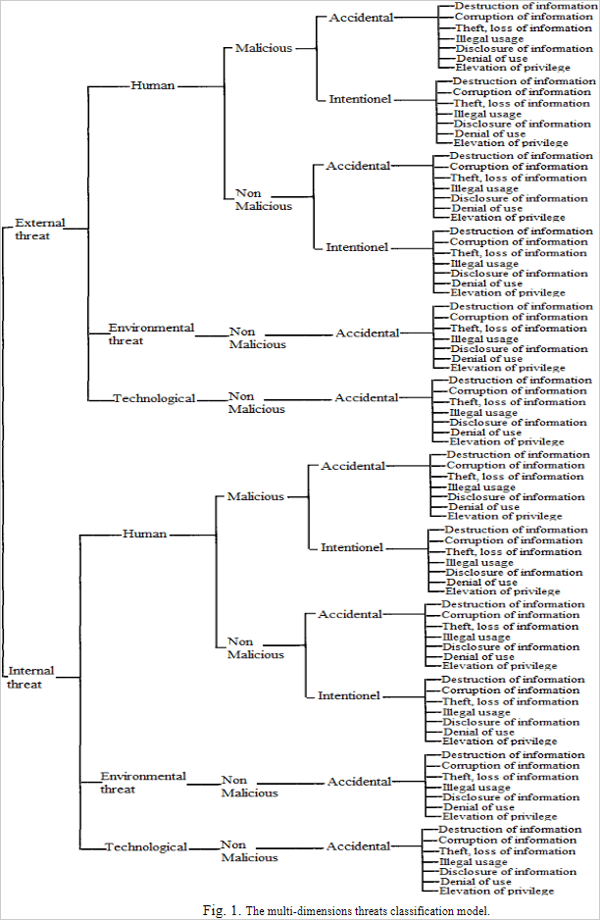
As you can see from the diagram above, web security threats can come from either:
- External sources (e.g. unauthorized users and natural disasters) or
- Internal sources (e.g. an employee with admin access to the site, server, or a network account).
Add in human, environmental, and technological agents with malicious or non-malicious motivation and accidental or non-accidental intent, and the security threats posed by any combination of these factors are further multiplied.
To put it simply…
Web Security is Freaking Complex!
A failure in any part of the system can threaten the security of the whole.
Even in situations where cyber attackers are not directly involved (e.g. natural disasters), these threats can create security blind spots that could impair your site and lead to:
- Destruction of information – e.g. deletion of important files or data.
- Corruption of information – e.g. corrupted database tables and files.
- Disclosure of information – e.g. exposing confidential data to unauthorized users or the general public.
- Theft of service – e.g. data theft or misuse, stealing server resources, etc.
- Denial of service – e.g. a Distributed Denial of Service attack (DDoS).
- Unauthorized elevation of privilege – e.g. exploiting a weakness in the system to gain admin privileges to the site or network,
- Illegal usage – e.g. using the site to attack other sites, spread viruses, run scams, identity theft, etc.
To prevent sites from being hacked, damaged, or disrupted, then, all threat factors in this multidimensional security beast need to be considered.
Now that we understand the enormity of what we’re dealing with, let’s narrow down how to tackle this web security beast.
We’ll focus on how to prevent your sites from being hacked by addressing the following areas:
- Mitigating Web Security Risks
- Defence is Your Only Plan of Attack
- Securing 95% of Vulnerabilities Against Hackers
1. Mitigating Web Security Risks
Many things can go wrong outside of your website and create an opportunity for hackers to get into your site.
These things include:
- External Services – who and where you purchase services from or outsource to, including hosting, plugins, themes, other website developers, etc.
- Processes and methods used to build, secure, and manage sites.
- Human vulnerabilities – inadequate knowledge, understanding, experience, and skill level of security-related issues.
Mitigating Risks from External Services
As a WordPress developer, your main service providers include the following:
- Your hosting company and data centers.
- Third-party plugin and theme developers.
- Integrated third-party platforms and software.
- Outsourced developers, contractors, etc.
Data Centers
Webhosting companies typically own or lease space to house their servers within multiple data centers located around the world.
All of your hosting company’s hardware, data, and information processing takes place inside data centers, so it’s important for data centers to take physical and digital security seriously to mitigate all threats and risks of attacks and damage, and to ensure the safety and security of the servers housing your websites and data.
Most developers choose their web hosting company and the web host chooses their data center(s). Both hosting companies and data centers, however, have a shared responsibility to ensure website security.
Data Center responsibilities for ensuring security include managing things like:
- Environmental controls – electronic equipment generates heat that can lead to failure, so it needs to operate at a safe temperature.
- Backup power supplies – servers need to keep running even if the main power grid unexpectedly goes down.
- Employing advanced security methods – this includes CCTV surveillance systems and technologies to ensure that hardware and people don’t enter or exit the center without approval, such as using trap rooms with biometrics and limited security access, single-entry doors (only one person allowed in at a time), server cages that enclose, protect, and segregate servers with sensitive data and equipment, metal detectors, etc.
- Securing facilities – this includes employing guards and installing protective measures like bulletproof glass, high-impact crash barriers, weatherproofing, fire suppression systems, etc.
Your Hosting Company
Focusing on areas like server speed and reliability or recommending companies based on plan pricing, affiliate commissions, and reseller incentives without prioritizing security can put your clients’ sites at risk.
Performance factors and economic benefits should not be discounted, but it’s also important to evaluate your host’s commitment to security.
95% of breached records in 2016 came from three industries and technology was one of them (government and retail were the others). Companies that store a high level of personally identifiable information (PII) in their records are very popular targets. So, it’s important to know how your hosting company stores data and what active and passive security measures are in place to protect it.
Some hosting options are more secure than others. We have written a detailed guide on different types of hosting, including which types are more secure and how to choose the right type of hosting for your needs.
Understanding the network redundancies in your host’s infrastructure is also important. What happens if a network server or a router fails or a component is breached and hacked into? How are your sites isolated and protected from network incidents and service disruptions caused by security breaches?
When evaluating a host, find out what kind of security measures are built into their hosting management and servers. Does your plan include server-side firewalls that proactively prevent malicious codes from entering the network (e.g. WAF), security features for encrypting and transmitting data like SSL, SFTP, and CDN?
What about file scanning, dedicated IPs, two-factor authentication (2FA), nightly backups and one-click restores, and a secure staging area for developing client sites, performing maintenance updates, and installing or testing new applications without leaving your websites vulnerable and exposed to attack?
Also, if despite all security measures, your site ends up being compromised, what kind of security guarantees and support does your web host offer?
Here at WPMU DEV, for example, we not only offer affordable, blazing fast, and secure managed WordPress hosting, but we also provide members with a dedicated 24×7 helpdesk for all WordPress-related issues (including security) and we’ll help you clean your hacked sites. We also provide extensive documentation covering all of our hosting security features.
If you’re serious about protecting your sites from hackers, you should expect nothing less than a total commitment to web security from your hosting provider.
Mitigating Risks from Third-party Sources
Although WordPress is a secure platform, it’s hard to avoid using third-party plugins, themes, and integrations with other platforms.
Any vulnerability in a third-party solution can open the door to hackers and lead to a compromised website.
To minimize risk when using third-party solutions, only download plugins from trusted sources (and themes), use reputable third-party platforms in your site integrations, and always keep your WordPress site up to date.
An excellent resource to check before installing any third-party solutions is the National Vulnerability Database.
For example, while writing this article, I did a quick search of the database on “WordPress” and over 3,000 results popped up, many listing vulnerabilities in WordPress plugins and themes (I also ran a search on “WordPress themes” which brought up 180+ theme vulnerabilities).

(As a point of interest, when we wrote an article about searching for WordPress vulnerabilities almost a decade ago, we looked at eight years of previous data and found that security vulnerabilities reported for WordPress core were trending downward, but issues reported for 3rd-party plugins were trending upward. We plan to revisit this in the near future and we’ll report our findings here, so watch this space!)
Mitigating Risks from Internal Processes
To keep things simple, let’s divide everyone into two groups:
- People you outsource services to (e.g. other web developers, remote workers, etc.)
- People you provide services to (e.g. your clients) – we’ll address this group later.
Suppose you own a web development agency and you employ/outsource other people. Every person in your business is a potential security threat. Your partners, staff, outsourced contractors, remote workers…and — from your client’s perspective — even you!
For example:
- You outsource technical work to someone with such high-level skills that no one else can understand or figure out what they are doing.
- Someone in your team with network access has been careless with a password or an email attachment.
- A remote worker with access to your systems and data is working from an unsecured wi-fi location.
In the introduction section, I pointed out that:
- 64% of companies have experienced web-based attacks.
- 43% of cyber attacks target small businesses.
Do the maths and you will quickly realize that some of your clients are bound to experience a cyber attack.
For example, if you are looking after 10 small business client sites, there’s a good chance that 2 or 3 of those websites will be targeted by hackers (10 x 64% = 6.4 sites x 43% =2.75 sites).
To reduce the probability that your business is responsible for client sites going down, it’s important to develop and implement internal security policies and guidelines covering areas like:
- Passwords & Accounts – This includes specifying how often passwords should be changed, setting expiring passwords and accounts, revoking access for employees who leave or are terminated, archiving, storing, and deleting stale data and sensitive information, etc.
- Use of BYOD (Bring Your Own Device) equipment – Do you allow staff, outsourced, or remote workers to use their own phones and laptops? If so, what security measures can you implement to store and handle proprietary data and client information on their devices securely? What happens if they delete important data accidentally or maliciously from your systems or server? Do you have a Mobile Device Management (MDM) policy giving you the power to wipe their devices clean remotely if their devices are stolen or lost?
- Training – If you employ remote workers make sure that they know how to securely log in and work remotely. Also, consider implementing training programs for employees, especially those in roles that are vulnerable to cyberattacks, and give them options to develop preventative and defensive skills and understand security best practices.
- Periodic Reviews & Evaluations – Just like software, the security of your business also needs to be reviewed, revised, and updated on a regular basis. Conduct periodic assessments of your internal security practices and policies to identify and patch up any weaknesses.
For additional tips on implementing security practices in your business or work environment, check out this great list of cybersecurity tips.
Now that we have looked at threats that can allow hackers into your business, let’s look at protecting ourselves from threats that can allow hackers into your website.
2. Defence is Your Only Plan of Attack
You’ve done all you can to mitigate security risks from external threats. You’ve chosen a web host that takes security seriously and runs servers from a data center more secure than Fort Knox. You only install third-party plugins and themes from reliable and trusted sources and integrate with established third-party platforms. Your workplace has implemented best security practices.
All that’s left now is to build amazing WordPress sites for your clients and make sure they’re impregnable fortresses to hackers.
Consider this quote from Sense of Security, a leading IT security firm on the escalation of the cybersecurity arms race:
Just as the advancements in technologies help security professionals identify and neutralise potential threats more effectively, it also provides the tools for hackers to undertake larger, more complex attacks. And these attacks are evolving faster than our defences can keep up.
Web security is not just a classic case of good guys vs bad guys, it’s also good guys training bad guys to become even badder guys!
As a web developer focused on building websites and not “cybersecurity weapons” the best you can do is try to keep up and defend as best as you can.
The more you know and understand about security-related issues, the better you will be able to defend sites from cyberattacks, hackers, malicious bots, etc.
To help you with this, we have written many in-depth articles and step-by-step tutorials on WordPress security and how to harden WordPress sites.
So, in this section, I’ll just provide you with a list of articles and tutorials that will turn you into a WordPress security pro.
If You’re a New WordPress Developer
If you’re just starting out as a web developer, we recommend checking out some of our hosting tutorials related to security, like understanding server file permissions, SSL, and WAF.
Also, make sure you understand why hackers want to target your WordPress site and how to scan a WordPress site for malware.
If your client has a small budget, check out how to secure a WordPress site for free.
We also recommend getting these quick and easy WordPress security vulnerability fixes into your tool belt.
Once you’ve got the basics covered, it’s time to…
Become A WordPress Security Pro
Start by checking out our Ultimate Guide To WordPress Security.
Next, go through our checklist for securing a WordPress site, checklist for making your site hacker-proof (with a downloadable PDF so you can tick off the boxes), and our guide to security resources for WordPress.
Also, check out our WordPress security expert interviews for some great tips on what WordPress security experts do to keep their clients’ sites safe and protected from hackers and malicious threats.
As part of developing your security expertise, make sure to also become familiar with resources like our DDos protection guide and how to test your WordPress site security.
And if your site has been hacked, make sure to head over to this post and learn how to clean up a hacked WordPress site.
Use Defender for Smart WordPress Security
As stated earlier,
“There is a hacker attack every 39 seconds.”
If you don’t believe these statistics, you can confirm this yourself by installing our WordPress security plugin, Defender.
Defender sends out a notification and logs every time someone tries to hack your site.

Defender blocks hackers at every level and adds layers of protection to your site. With just a few clicks, your WordPress site is protected from brute force attacks, SQL injections, cross-site scripting XSS, and many other WordPress vulnerabilities and hacks.
Defender also runs malware scans and antivirus scans and provides IP blocking, firewall, activity logs, security logs, and two-factor authentication login security.
And that’s just the free version of the plugin.
Check out our Defender WordPress security plugin tutorials to see everything that this plugin does and to learn how to easily configure it on your clients’ sites (tip: our WordPress management console The Hub makes it even easier and faster to install and configure Defender on multiple WordPress sites.)
3. Securing 95% of Vulnerabilities Against Hackers
As I stated earlier,
“95% of cybersecurity breaches are caused by human error.”
Choosing a super-secure web host is not a problem. (You can do this with one click here.)
Implementing internal security processes in your business takes some effort, but it’s also not a problem.
Hardening WordPress security…not a problem either. You can find everything you need to know to make WordPress impenetrable to hackers right here on this site.
The main challenge when it comes to preventing hackers is how to make sure people don’t make errors when “to err is human.”
If you can figure that one out, you’ll have protected your clients from 95% of all security vulnerabilities on the web and put hackers permanently out of a job. 😉
Until this happens, however, you’ll just need to be patient with people. Help them implement good security practices and develop better online safety habits, starting with basic things like password security, avoiding email phishing scams, etc.
Also, encourage your clients to implement good security policies in their workplace and train and educate them as best as you can on ways to become more aware of threats and how to reduce security risks.

Remember that in the end, no matter what we do, we are all human and we are all going to make mistakes at some point or another.
Also, everyone in the world has problems. Addictions, resentments, job dissatisfaction, greed, opportunism, and disgruntled personalities can manifest at any time in the work environment and these can become a potential security threat too.
So, unless your clients are perfect human beings without problems, you’re still left with 95% of security vulnerabilities to deal with.
The Best You Can Do To Not Get Hacked
Web security threats are multidimensional and cybersecurity is an escalating arms race, so hackers will always have new opportunities to identify weaknesses and vulnerabilities on many levels.
The best you can do to not get hacked is to do your best.
Mitigate as many of the risks as you can, implement best security practices at every level, keep learning and improving your knowledge of web security, stay vigilant, and help your clients do the same.
If you need expert help with anything WordPress-related contact our 24/7 support team. We’re the good guys fighting on your side.
Source: premium.wpmudev.org