I have minimal Ubuntu Linux 18.04 LTS server setup in the cloud. I read that one can configure Ubuntu Linux to download and install security updates when released automatically. How can I set up automatic security updates on Ubuntu Linux 18.04 or 16.04 LTS system?
Introduction: It is true that the Linux server security is an essential task for sysadmins. One of the most fundamental ways to keep server or desktop secure is by installing security updates to patch vulnerabilities on time. One can use the apt-get command or apt command to install security updates. This page shows you how to configure Ubuntu Linux system to install security updates automatically when released by Ubuntu security team.
Ubuntu Enable & Setup Automatic Unattended Security Updates
You may be wondering why do I need an unattended way and installs security updates? Applying updates on a frequent basis is an important part of keeping systems secure. By default, updates need to be applied manually using package management tools. However, you can choose to have Ubuntu automatically download and install important security updates.
Step 1. Install unattended-upgrades package
Warning: Some security risks associated with running unattended software upgrades without supervision do exists, but there are also benefits. Use your judgment when in doubt.
Type the following apt-get command or apt command to install unattended-upgrades package:$ sudo apt install unattended-upgrades apt-listchanges bsd-mailx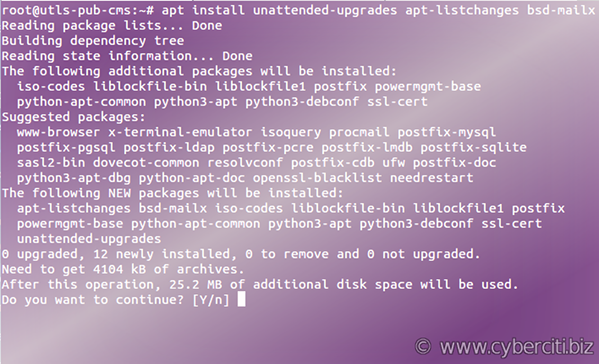
Step 2. Ubuntu enable unattended security updates
Run the following command:$ sudo dpkg-reconfigure -plow unattended-upgrades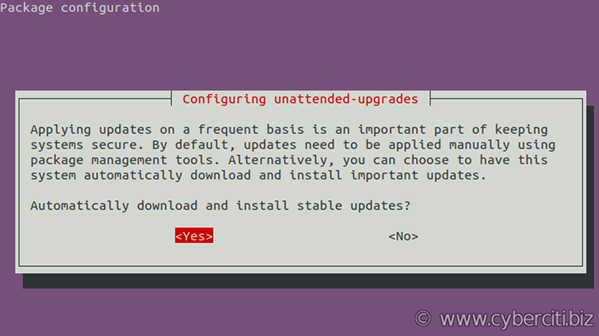
You should see /etc/apt/apt.conf.d/20auto-upgrades file created due to above command. One can view the same with cat command:$ cat /etc/apt/apt.conf.d/20auto-upgrades
Sample outputs (make sure it is as follows; if NOT update it manually):
APT::Periodic::Update-Package-Lists "1"; APT::Periodic::Unattended-Upgrade "1"; APT::Periodic::AutocleanInterval "7"; APT::Periodic::Unattended-Upgrade "1"; |
Step 3. Configuration file
You need to edit the file named /etc/apt/apt.conf.d/50unattended-upgrades using a text editor such as vim command or nano command:$ sudo vi /etc/apt/apt.conf.d/50unattended-upgrades
Make sure config is as follows:
Unattended-Upgrade::Allowed-Origins { "${distro_id}:${distro_codename}"; "${distro_id}:${distro_codename}-security"; // Extended Security Maintenance; doesn't necessarily exist for // every release and this system may not have it installed, but if // available, the policy for updates is such that unattended-upgrades // should also install from here by default. "${distro_id}ESM:${distro_codename}"; // "${distro_id}:${distro_codename}-updates"; // "${distro_id}:${distro_codename}-proposed"; // "${distro_id}:${distro_codename}-backports"; }; |
One can skip packages to not update (optional):
// List of packages to not update (regexp are supported) Unattended-Upgrade::Package-Blacklist { "linux-image"; "vim"; "nginx"; }; |
You need to configure an email address to get email when there is a problem or package upgrades. Of course you must have working email setup to this work:
//Send email to this address for problems or packages upgrades // If empty or unset then no email is sent, make sure that you // have a working mail setup on your system. A package that provides // 'mailx' must be installed. E.g. "user@example.com" Unattended-Upgrade::Mail "notify@server1.cyberciti.biz"; |
Save and close the file. Finally edit the file named /etc/apt/listchanges.conf using a text editor such as vim command/nano command:$ sudo vi /etc/apt/listchanges.conf
Set email address from:email_address=root
To:email_address=notify@server1.cyberciti.biz
Save and close the file.
Conclusion
You learned how to install and configure the unattended-upgrades package to automatically install updated packages, and can be configured to update all packages or install security updates. For more info see this page.

