Brevo vs SendGrid: Which One Should You Use for Your Ecommerce Business?
Brevo and SendGrid are two leading email platforms used by ecommerce businesses around the world. Whether…
Brevo and SendGrid are two leading email platforms used by ecommerce businesses around the world. Whether…
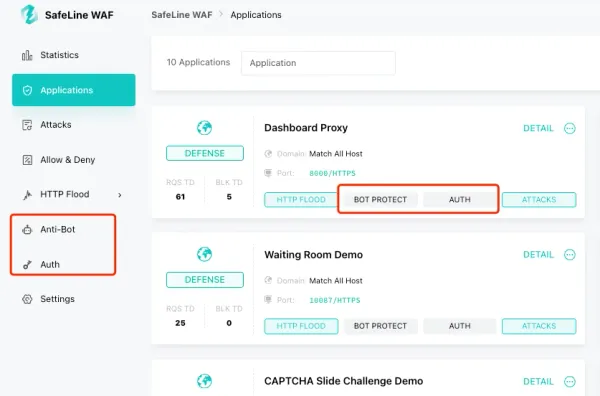
Running a Homelab is exciting. You get to experiment with services, try new software, and even…

A significant part of the website development practice is always keeping in mind that security is…

As a natural continuation to our October’s Cybersecurity thematic series, this post’s goal is to highlight…

The Google Ads API will no longer accept new adopters of session attributes or IP address…

Do you have a website? Has it ever been compromised? Statistics show that in the average…

The Toronto Raptors had their fans cheering and managed to capture the hearts of Toronto residents…

WordPress brute force attacks are a complex matter. Brute-forcing is one of the first, most primitive…

When you hear about technologies like Docker, Podman, or Kubernetes, the term “container” is never far…

Think of Terraform as a construction manager. Resources are the buildings you construct. Data sources are…

So here we are, standing firm at the beginning of a new decade. 2019 has been…

Did you know that many security breaches happen through assets companies didn’t even know they had?…

Media servers have exploded in popularity over the past few years. A decade ago, they were…

The servers that run our applications, our businesses, all depend on the stability and underlying features…

You’ve already seen how to monitor CPU and memory usage with top and htop. Now, let’s…

Ever wonder how security pros find those hidden entry points before the real testing even begins?…

Six months after Laravel 7, on September 8th, 2020, Laravel 8 was officially released — right…

SunFounder’s Pironman cases for Raspberry Pi are a huge hit. This bestselling device converts the naked…

Search engine optimization (SEO) is a catch-all term for the steps you can take in improving…

Minecraft is a game where you get a gaming experience of fantastic adventure with limitless possibilities…

Are you running a website or an online store and finding it hard to get it…

The last time I reviewed the Pironman 5, I thought that it was the most amazing…

Here at FastComet, we’re passionate about lightning-fast websites. So much so that we often post various…

The other day, a friend and I were talking about virtualization, spinning up virtual machines (VMs),…