Why GitHub? Here's How I Push Git Repositories Straight to My Linux Server
At some point, I realized that almost every project I worked on followed the exact same…
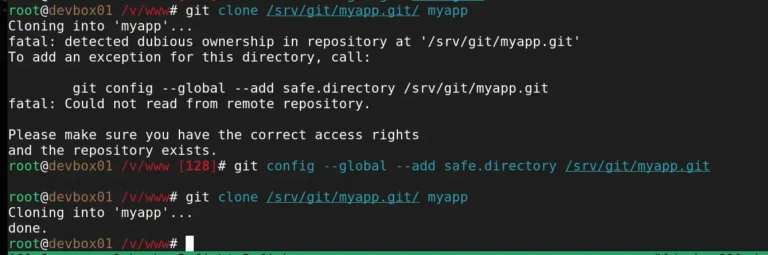
At some point, I realized that almost every project I worked on followed the exact same…

Zeroport has raised $10 million in a funding round to accelerate product development and expand internationally,…
Running a Homelab is exciting. You get to experiment with services, try new software, and even…

Beachgoers in Australia are on high alert following four shark incidents in New South Wales in…

They say you can tell a lot about someone by the company they keep. All of…

U.S. based Dispersive, a company delivering stealth networking for ultra-secure, high-performance communications, has secured a place…

On December 14 2025, a terrorist attack occurred at Bondi Beach in Sydney Australia, leaving 15…

Dog attacks are on the rise in Australia. The most recent data from the Australian Institute…

Late last year, the New South Wales government announced an additional A$9.5 million in funding to…

Want the French Audience to buzz around your website so they may browse its information without…

A significant part of the website development practice is always keeping in mind that security is…

Once discussed primarily as a compromise between legacy infrastructure and public cloud ambitions, hybrid cloud is…

WitnessAI has secured $58 million in strategic funding, underscoring growing investor confidence in technologies designed to…

Cybersecurity until recently has been a very underground topic. Most people took it for granted, but…

Datavault AI partners with IBM and Available Infrastructure to deploy secure, low-latency edge AI across New…

Wrapping things up in our October’s Cybersecurity blog post series, as the saying goes we have…

As digital transformation accelerates, hybrid cloud architectures have emerged as a dominant enterprise model. By combining…

Server hardening is no longer a quiet background task handled exclusively by system administrators. As cyber…

I get it, these are uncertain times. Organic traffic is dropping like a rock, and new…

CrowdStrike has moved to address what it describes as one of the fastest-emerging risks in enterprise…

Stocking your online store with high-quality, desirable products is only part of building a successful and…

Fortinet and Arista Networks have moved to formalize a joint approach to securing and operating AI-focused data center…

As enterprises deploy AI across cloud environments, concerns around securing data, models, and infrastructure are drawing…

In the wake of Sunday’s tragic Bondi shooting, conspiracy theories and deliberate misinformation have spread on…