Do you have a website and want to set up your DNS records? Using Cloudflare makes it a lot easier to set up your DNS records than if you were to manually set them up with software like bind9. This article will describe step-by-step how to set up Cloudflare DNS for your domain.
A Quick Overview Of DNS
DNS (Domain Name System) in a nutshell is the system that translates domain names like example.com to IP addresses for which computers can understand. For example, one IP address which google.com owns is 172.217.24.206.
Most likely you wouldn’t want your users to type in something like http://172.217.24.206 into a browser (this redirects to google.com). You most likely would want to own a domain name like example.com where your users would go, which is easy to remember. But in order for your domain like example.com to work, it must have DNS set up.
For years, I set up DNS manually on Linux servers with bind9. But, the setup is at times very complicated, and one small mistake can prevent your domain from working properly. I’ve found using Cloudflare for my DNS set up makes my sites faster, more secure, and the setup is easier than using software like bind9.
Step 1. Log Into Your Cloudflare account
If you don’t have a Cloudflare account, read the following article how about how to set up a Cloudflare Account.
Step 2: After Logging In, Choose The Website That You Want To Control In Cloudflare
After logging in, you will need to choose which domain to control. (This assumes you have already set up a domain with Cloudflare). I will choose my domain linuxwebdevelopment.com in Cloudflare to control.
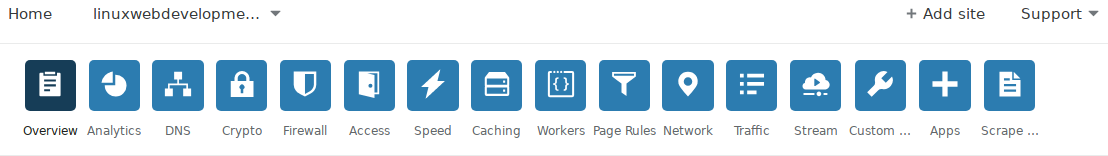
Step 3. Navigate The Cloudflare Top Menu Bar And Choose DNS
On the top menu button, click on the DNS button. See the screenshot below for an image of that. The DNS button is the 3rd icon from the left.
Step 4: Choose Which DNS Records That You want To Set Up
After you are in the DNS section, if you have previous records, you should see something like the following image.

The main types of DNS records I set up are: A records, MX records, and TXT records, but there are also several other DNS records you could use.
A Records
If you want to point to a web server, you will need want ‘A’ records. A records are necessary for domains and subdomains to work.
I always use A records since they are the record types that map a domain or subdomain to the IP address of the web server. For example, if one wanted to go to linuxwebdevelopment.com or subdomain1.linuxwebdevelopment.com, an A record would be needed for both.
MX Records
If you want to have email for your domain, you must have at least 1 MX record. I usually have 3 MX records set up. Having multiple MX records basically is just to have more resiliency in case there are some problems.
For example, if I wanted to have the email address someemailaddress@example.com, and if I owned example.com, I would need to have at least 1 MX record pointed to some email server or else that email address would never work.)
You should contact your email service provider or go to their website to find out what the MX records should be. If you use Google G Suite, you can find out here about those MX records here. If you use Zoho to host your domain’s email, you can go here to learn how you should set up those MX records.
TXT records
I generally only use TXT records for use with DKIM and SPF records. I use SPF and DKIM records so that when I send emails from my email addresses for my domains, it is much less likely to go to spam, since the receiving email server can test with a very high probability the email is not forged.
TXT records are also uses for various other reasons such as verifying that you own a domain for another website.
Below is an image of what some TXT and MX records might look like.

Additional DNS Record Types
A, MX, and TXT are by no means the only type of DNS records there are, just the ones I use the most. For a list of all of the DNS record types, read more here.
Step 5: Set Up The DNS Records
Now that you know which DNS records you want, set them up. I will show you how to set up two A records in this section.
How To set up A Cloudflare DNS Record
To make a new DNS record in Cloudflare, simply go near the top where there are input boxes below the search bar which says “Search DNS Records” and add your records one-by-one there.

The default option for adding a DNS record is an A record, but you can just click on the drop down menu as you can see below.

Setting Up An A Record For A Domain In Cloudflare
If you wanted to add the the A record for the base domain, such as linuxwebdevelopment.com, you would choose A record, type in the domain name in the Name box, then type in the IP address for the web server in the IPv4 address box.
For an example, see below where I made an A record for linuxwebdevelopment.com using IP address 123.456.789.123.

For your own domain, you would just substitute “linuxwebdevelopment.com” for own your domain, and substitute 123.456.789.123 for the IP address of your web server. If you don’t know the IP address of your web server, you may need to contact your web host to find that information out. Finally, click on the blue “Add Record” button. Soon after, you will see that record added to the list of your DNS records below.
Setting Up An A Record For A Subdomain In Cloudflare
Setting up an A record for a subdomain is just like setting up an A record for the main domain. If you had a subdomain named subdomain1.linuxwebdevelopment.com, you would just type in subdomain1 in the Name box, and then type in an IP address in the next box. I’ll assume that the IP address will be the same at 123.456.789.123. Finally, click on the blue “Add Record” button. Soon after, you will see that record added to the list of your DNS records below.

Quick Notes About Subdomains:
Technically, a subdomain doesn’t have to have the same IP address as the base domain. For example, I could have linuxwebdevelopment.com on one web server with IP address X, and subdomain1.linuxwebdevelopment.com on another web server with IP address Y. In fact, subdomains can be basically be treated as separate websites. I have domains where I have multiple subdomains on different IP addresses with some being hosted with Apache and others being hosted with Nginx and on each of those subdomains, I have different apps or websites running.
Editing A Previously Added DNS Record In Cloudflare
Editing a previously added DNS record in Cloudflare is easy. Just scroll down and find the record you want to edit. Then, double click in the IP address box for your record or double click in the Name box,
and edit as you like. Though, you cannot edit the type of DNS record in Cloudflare. If for example, you meant to make an AAAA record instead of an A record, you will need to delete the A record by clicking on the “X” button on the right side of the record and then make a new record of what you want.

Using An HTTP Proxy For Your A Records With Cloudflare
Note the icon with an orange cloud with a grey arrow going through it for some A records.

You can select or deselect the orange click by clicking on the cloud icon to the right of the respective record. Selecting the orange cloud will hide your server’s IP address from others for A records, AAAA records, and CNAME records in Cloudflare, and it will use Cloudflare as an HTTP proxy for that record. That means that people who go to your site, will see Cloudflare’s IP address and not your server’s IP address.
Basically, this hides the IP address of your site, and also makes it much harder for your site to be attacked. If you hover over the icon when it is selected, you should see some text saying “DNS and HTTP proxy”.
If the orange cloud is unselected, you should see an icon with a grey cloud and grey arrow going around that cloud. This means that the IP address of your A record is “exposed” meaning that if someone checks the server’s DNS records, that it could see the direct IP address of your web server. This means that the person could much more easily attack the web server. Cloudflare will likely give you a warning about this.
If you have DNS and HTTP proxy (using the orange cloud), the IP address is set to be one of Cloudflare’s, and so it’s a lot more secure. The IP address of your A record is hidden, and it doesn’t cost any more. This is something I highly recommend, and do for all of my A records. I see very few reasons one shouldn’t hide their IP address for their A records. This option of protecting the IP address is only available for A, AAAA, and CNAME records.
I highly recommend you use the option of hiding the IP address with an HTTP proxy for better security. In addition, it may make your site faster if it is on a VPS because you might receive less spam traffic to the server.
Step 7 (Optional) Cloudflare Crypto / Security Setup
In addition to DNS records, you may also want to set up the security options for your site. To get to the Crypto / Secruity settings, go to the the top menu button, and click on the Crypto button. See the screenshot below for an image of that. The Crypto button is the 4th icon from the left and has a logo of a lock.

Cloudflare SSL (HTTPS) Setup
Cloudflare provides free SSL certificates for domains for use with HTTPS. I use Cloudflare’s certificates on most of my sites. The difficulty of the SSL set up with Cloudflare depends on exactly how secure you want it to be.
There are 4 main options for SSL Off, Flexible, Full, and Full (strict).

According to Cloudflare, these are what the different options mean:
Off: No secure connection between your visitor and Cloudflare, and no secure connection between Cloudflare and your web server either.
Flexible SSL: A Secure connection between your visitor and Cloudflare, but no secure connection between Cloudflare and your web server. You don’t need to have an SSL certificate on your web server, but your visitors still see the site as being HTTPS enabled.
Full SSL: A secure connection between your visitor and Cloudflare, plus a secure connection (but not authenticated) between Cloudflare and your web server. You will need to have your server configured to answer HTTPS connections, with at least a self-signed certificate.
Full SSL (Strict): A secure connection between your visitor and Cloudflare, plus a secure and authenticated connection between Cloudflare and your web server. You will need to have your server configured to answer HTTPS connections, with a valid SSL certificate. This certificate must be signed by a certificate authority that is trusted by Cloudflare, have an expiration date in the future, and respond for the request domain name (hostname).
I often go with the Flexible SSL setting because I find very easy to set up, but you could also go with full or full (strict). With the Flexible SSL setting (assuming I just want the Cloudflare SSL), for my domain in Apache, I only need the to set up the config file linuxwebdevelopment.com.conf in Apache.
If I just use Flexible SSL, the config file linuxwebdevelopment.com-le-ssl.conf is unnecessary, and the SSL for my site linuxwebdevelopment.com works fine without it.
Due to the complexity of setting up an SSL certificates on a server at times. Setting up a server with HTTPS and spending hours to find out it’s not working because of the SSL configration can be extremely annoying. For these reasons, I usually go with Flexible SSL.
Additionally, when using subdomains or domains with Nginx and Node.js servers, I also usually just use the Flexible SSL setting. That way, https will work without me having to configure the Nginx config files for use with https.
Though, if security is very important to you, I’d recommend going with either Full or Full (secure) .But at least for basic security and SEO, the flexible option is good.
Using HTTPS For Security And SEO
Setting up HTTPS for your site is a great thing that is good both for security and also for SEO. Google now uses HTTPS as a ranking signal.
Additional Optional Cloudflare Cryptography Settings
Always Use HTTPS Option
If you scroll down on the page, you should see an option which says “Always Use HTTPS Option”. I think by default, it is disabled, but I usually enable it. Its brief text succinctly describes it, “Redirect all requests with scheme “http” to “https”. This applies to all http requests to the zone.” Basically, it means that uses will always see https in a url. For example, if you own example.com and a user goes to http://example.com, it would be redirected to https://example.com and all other urls on the domain would use https. I usually enable the option Always Use HTTPS.

Miscellaneous Cloudflare Crypto/ Security Options
Some additional security settings I would recommend enabling are Opportunistic Encryption, Onion Routing, TLS 1.3, and Automatic HTTPS Rewrites. I talk about each of those below.

Opportunistic Encryption
Regarding Opportunistic Encryption, the page says, “Opportunistic Encryption allows browsers to benefit from the improved performance of HTTP/2 by letting them know that your site is available over an encrypted connection. Browsers will continue to show “http” in the address bar, not “https”. I see no benefit in disabling the Opportunistic Encryption. I think you should enable it.
Onion Routing
Regarding Onion routing, the page says “Onion Routing allows routing traffic from legitimate users on the Tor network through Cloudflare’s onion services rather than exit nodes, thereby improving privacy of the users and enabling more fine-grained protection.” With this option, I see no advantage to disabling it and only upsides to enabling it. While I have no idea how many people visit my sites using Tor, I’d rather make it more secure for them.
TLS 1.3
The page says, “Enable the latest version of the TLS protocol for improved security and performance.” This again is something I’d recommend.
Automatic HTTPS Rewrites
The page says “Automatic HTTPS Rewrites helps fix mixed content by changing “http” to “https” for all resources or links on your web site that can be served with HTTPS.” If you are going to use HTTPS on your site, this is something I highly recommend as it would be better to have HTTPS for everything. With this, you can avoid warnings that Google Chrome, Firefox, or other browsers may show in a window if the main page uses HTTPS, but there are some insecure elements using http such as a link to an image.
Conclusion
If you own a domain, you MUST set up DNS for the domain to work properly. Using Cloudflare makes setting up DNS much easier than manually configuring all of the DNS files on your server, will likely make your site faster because of better DNS configuration, tweaking and less spam traffic. Additionally, using Cloudflare DNS will likely make your site more secure. If you set up DNS with Cloudflare, it can also be very beneficial both for SEO and for general security to use the cryto settings mentioned above.
Did you find this article about How To Set Up Cloudflare DNS useful? If so, please share this article with your friends.
The post How To Set Up Cloudflare DNS appeared first on linuxwebdevelopment.com.