In this blog series, We will learn about encryption and decryption basics in a very casual fashion. We will start discussing from origin of cryptography and then learn about modern techniques.
One of the important and main techs in encryption is Cryptography.
Cryptography is a tech that is very, very common and which is used everywhere right now, whether any software as follows:
- Routers we use in our homes.
- WhatsApp we use to send and receive messages.
- Any site we are opening on HTTPS.
- And so on…
Now, At the same time, cryptography is very common, but it is extremely complex. Complex in understanding, implementing, and even using it correctly.
The Need for Cryptography
To answer this, let’s answer the following:
- Why do we need passwords on our phones?
- Why lock the door of our home when going outside and take keys with us?
The same is the answer to using cryptography – To ensure that the sender or receiver is the right one and they can only see the right form of data.
To understand how it works, let’s start with the old-age method known as Caesar Cipher.
Caesar Cipher
The Caesar Cipher is a type of substitution cipher in which each letter in the plaintext is shifted a certain number of places down the alphabet. This simple encryption technique is named after Julius Caesar, who used it to encrypt messages sent to his officials. The process of encryption is simple: a shift value ( also known as a key) is chosen, and each letter of the plaintext is shifted by that number of positions down the alphabet.
For example, with a shift of three, A would be replaced by D, B would be replaced by E, and so on.
Plaintext: Sahil
Shift(Key): 3
Ciphertext: Vdklo
To decrypt the message, the shift value is used in the opposite direction.
Ciphertext: Vdklo
Shift(Key): -3
Plaintext: Sahil
It is important to note that the Caesar Cipher is very easy to break and should not be used for any serious encryption purposes, as it can be broken by simple methods such as frequency analysis.
Here, the Algorithm is Simple: shift a letter N several times and then replace it with that letter and Continue this process till our plain text is Converted into cipher text.
A Caesar Cipher table is a tool that can be used to manually encrypt and decrypt messages using the Caesar Cipher method. It is a table that lists all of the letters of the alphabet and their corresponding encrypted or decrypted letters based on a chosen shift value (or key).
Here is an example of a Caesar Cipher table with a shift(Key) value of three:
| Plaintext | Ciphertext |
| A | D |
| B | E |
| C | F |
And so on …
With Caesar cipher, someone can easily reverse engineer this Caesar cipher text and decode the messages encrypted using this algorithm by identifying the pattern; one can easily determine the key. This was just an example to get the readers familiar with the cryptography and encryption decryption concepts.
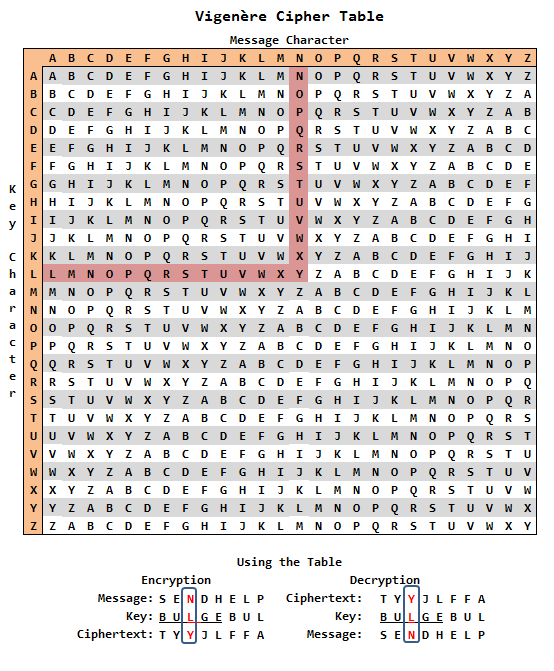
As we discussed, the Caesar cipher is less secure; there is a more secure algorithm than it, and its name is the Vigenere cipher.
This algorithm is more or less the same as Caesar’s cipher, but instead of rotating every word with the same number, here we rotate every letter with a different number, and the combination of these numbers is known as a key.
Let’s start with the same example to encrypt:
Plain text to encrypt — SendHelp
Key — BULGE
Cipher text we will get from the following table.
Now, all these algorithms we discussed till now are Symmetric algorithms — which means that the Same key is used for the encryption and decryption of the messages.
As we see here, we have two things in the encryption world: One is a Key, and one is an Algorithm.
Now, Consider a local example of our house lock and key. What should we do locking and unlocking mechanisms should be kept secret, or the key only be? If we have Too many algorithms, then maintaining them and passing them to every algorithm with data to decrypt the messages will be cumbersome and non-maintainable.
Due to all these reasons, We have some popular Algorithms that are kept open for the public, and only Key Management and how we can share the key remains the only problem for us.
Nowadays, AES is the most popular and secure algo used for encrypting data at rest, and many people are trying to break this algo for good reasons.
Now Comes Another Question:
When we encrypt the same Plain Text with the Same key, Should it result in the same Cipher text?
Well, the Answer to this is Yes/No. It depends on the use case and how much security we want.
Now, in the encryption, the Same Cipher text is produced every time. This is called Convergent Encryption.
Now, it depends on the IV(initialization vector). If we pass the same IV while encrypting data, then the Cipher text will be the same.
IV(Initialization Vector) Definition — An Initialization Vector (IV) in encryption is a random or semi-random value used to initialize a cryptographic algorithm’s initial state before it begins to encrypt or decrypt data. The purpose of an IV is to ensure that the same plaintext encrypted with the same encryption key results in different ciphertexts each time it’s encrypted. This property is crucial for security, particularly when encrypting multiple pieces of data with the same key.
Now the question arises when we need Convergent Encryption:
There are many use cases like, sometimes when we want to search for a name that is encrypted in the database; we have two ways here:
- Decrypt all the Names stored in the database, load them into memory, and search.
- Encrypt the name that came as an input for search and then search that cipher text in SQL Query.
Option two is more optimal and fast and will consume fewer resources. But to implement it, we need Convergent Encryption Algorithm.
Until now, we have heard about some important terms as follows:
- Cryptography
- Algorithm
- Plain Text
- Key
- Cipher Text
- Symmetric Encryption
- Convergent Encryption
- Initialization Vector
Please keep them in mind, as these are the generic terms used everywhere in the world of encryption and decryption.
In coming Blogs, we will gossip about some other things, like:
- Hashing
- Asymmetric Algorithms
- PKI Infrastructure
- Envelope Encryption
- and many more things
Stay tuned for the next part …


