Snap packages have been a topic of contention in the Linux space for a while now. Some complain about slower startup times. Others dislike the proprietary Snap Store backend. Then there are concerns about bundled dependencies sitting around without updates.
All of that hasn’t stopped Canonical from working on it, though. They have been busy making it faster and more secure, while shipping Snap versions of popular applications like Firefox on Ubuntu.
Now there is a new tool that might actually help with one of the major concerns surrounding Snaps. Alan Pope, a known voice in the Ubuntu community, has built a tool called SnapScope that scans Snap packages for security vulnerabilities.
SnapScope: Checking Snaps for CVEs
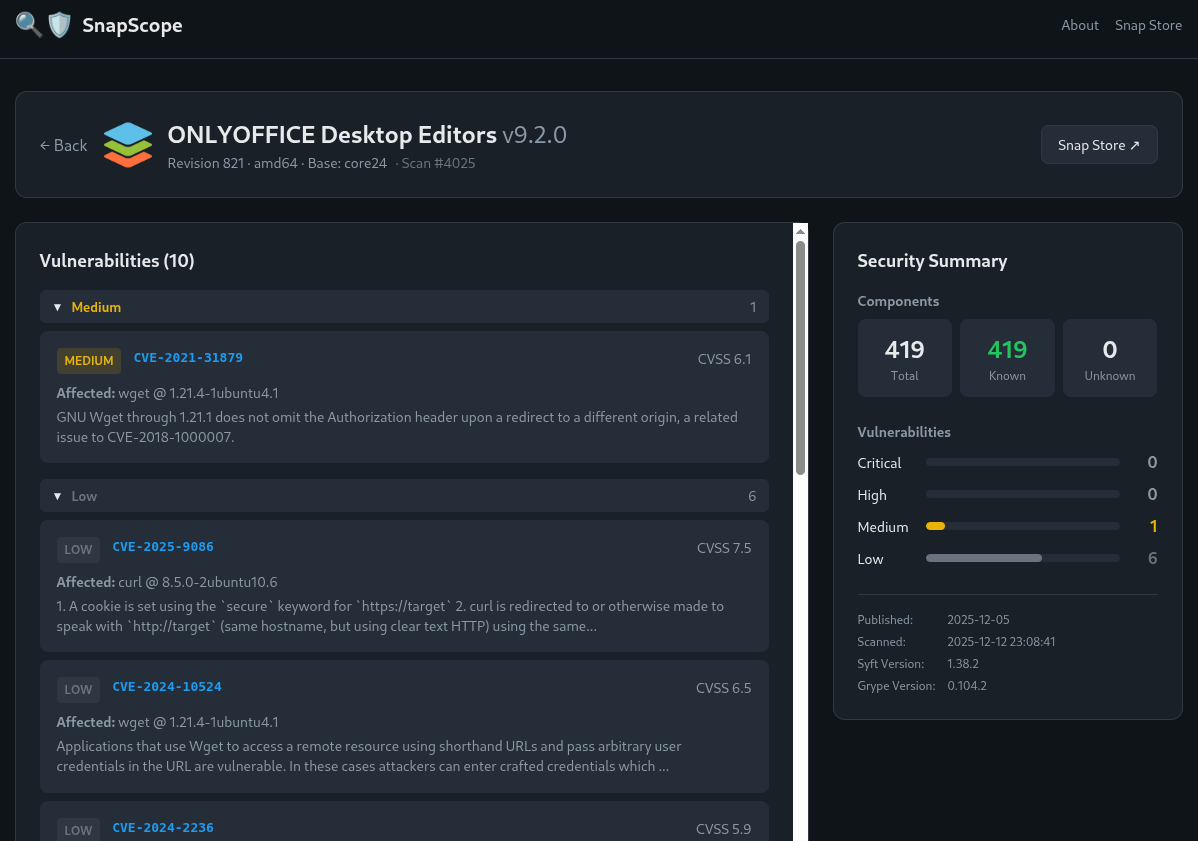
The website works both on desktop and mobile and is straightforward to use. You type a Snap package name or publisher into the search bar, and Snapscope scans it for known vulnerabilities. The results are broken down by severity: KEV, CRITICAL, HIGH, MEDIUM, and LOW.
Currently, Snapscope only supports x86_64 packages (with the possibility of other platforms being supported), and the vulnerability data comes from Grype, an open source scanner for container images and filesystems.
Each vulnerability entry shows the CVE ID, severity rating, and relevant links to learn more about it. The homepage also has two charts that show recently scanned packages and packages with the highest vulnerability counts.
Alan mentions that he vibe-coded this for Chainguard’s Vibelympics, a competition where developers throw together creative projects to win $1,000 that goes to a charity of the winner’s choice.
The tool itself takes a “no judgement, just facts” approach. It doesn’t tell you whether Snaps are good or bad. It just shows what vulnerabilities exist in the packages you search for.
If you are wondering: Who’s this for?
Well off the top of my head, sys admins who need to audit their Snap installations, developers maintaining Snap packages who want to know what CVEs they need to tackle, and security-conscious users who intend to check what they are installing before it touches their system.
Via: OMG! Ubuntu