THIS Is Where the Internet Lives
Check out Equinix and learn more about how they power the internet: https://eqix.it/4gioy31 What if I…

Check out Equinix and learn more about how they power the internet: https://eqix.it/4gioy31 What if I…

We are entering the new business season with a bang. We’re always trying to push the…
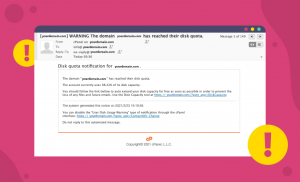
Since April of this year, some hosting providers have reported that their clients are receiving phishing…

WordPress 5.8 was a big one! After this important update, we have decided to create a…


Start using n8n with a VPS via https://hostinger.com/ncn8n + use code NETWORKCHUCK for a discount. #automation…

Want to deploy AI in your cloud apps SAFELY? Let Wiz help: https://ntck.co/wiz Can you hack…

As you may have already seen from one of our previous posts this quarter, we have…

Ever had one of those messages offering work from out of the blue on SMS/WhatsApp/Telegram/Signal? Well,…

Thanks to AnyDesk for supporting this event. They offer a superb tool for remote access and…

Start using n8n with a VPS via hostinger.com/ncn8n + use code NETWORKCHUCK for a discount. You…

Register today for the best rates available and use code NETWORKCHUCK to save. — https://ntck.co/blackhat2025 #ad…

Poor Pryia. We manage to see her last day of working in a scam call center….

Learn more about self-driving networks: https://juniper.net/provenAISee AIOps in the data center with Juniper’s interactive demo: https://juniper.net/chucklovesdatacentersStay…

Choosing the right WordPress plugins for your site can be daunting. That’s because of the sheer…

Are you really still using VPN? You need Twingate: https://ntck.co/twingate_telos If you’ve got AI anxiety about…

Every website owner should know that ensuring their website’s safety is essential. WordPress may already be…

Stay connected from anywhere–even Cisco Live. See how we keep our studio online with Twingate :https://ntck.co/twingate_ciscolive2025…

Running an online store means making sure every part of the shopping experience goes smoothly. So…

Register now with code NETWORKCHUCK to save $200 off in-person Briefings or $100 off a Business…

Here at FastComet, we strive to provide stable, secure, and feature-rich services while maintaining our affordable…

Thanks to Cisco for sponsoring me to come to CiscoLIVE 2025. This trip would not have…

Security is one of the major pillars our services here at FastComet are founded on. We…

Get a huge discount at https://vanta.com/chuck