FOSS Weekly #25.29: End of Ubuntu 24.10, AUR Issue, Terminal Tips, Screenshot Editing and More Linux Stuff
After Denmark and France, now we have another positive news from Europe as two major open…
After Denmark and France, now we have another positive news from Europe as two major open…
The rise of AI-powered coding tools has reshaped developer workflows worldwide. Interactive development environments are becoming…
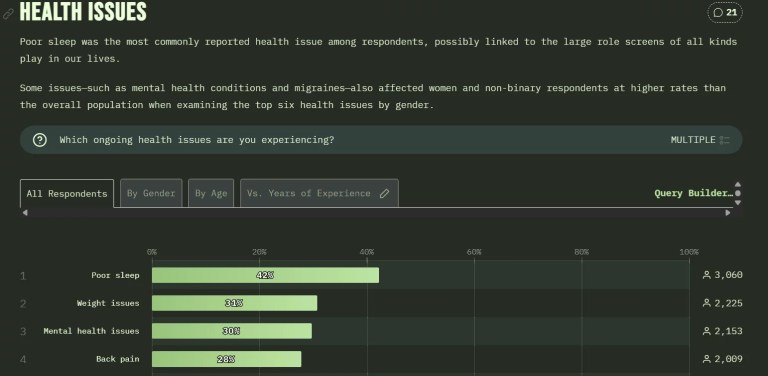
The State of Devs 2025 survey results have been released! While the survey doesn’t directly address…

I am using CachyOS on my primary system these days and pretty content with its performance….

Unlike previous updates where we might see evidence of some degree of reversal afterward, HC stands…

What is line length? Line length refers to the length of a container holding multi-line text….

Scroll-driven animations are fantastic! They empower developers to link the movement and transformation of elements directly…

According to Garrett, AI Overviews for local search are “still garbage,” and not much has changed…

9:20 AM – 9:50 AM: Pete Meyers. Principal Innovation Architect, Moz. The Infinite Tail: Keyword Research…

After Denmark, now the news is that French city Lyon is ditching Microsoft to set up…

When it comes to making strategic decisions about your content strategy, it pays to consider multiple…

Most file sharing today takes place through cloud services, but that’s not always necessary. Local file…

This is the fourth post in a series about the new CSS `shape()` function. So far,…

I was trying to update my CachyOS system with in the usual Arch way when I…

Now, let’s move on to automating monotony. I think for most people, we think of automation…
![Convince Your Boss to Send You to MozCon 2025 [Plus Bonus Letter Template]](https://wiredgorilla.com/wp-content/plugins/wp-fastest-cache-premium/pro/images/blank.gif)
Asking for budget to attend a conference can sometimes feel awkward. You don’t want to sound…

And we achieved the goal of 75 new lifetime members. Thank you for that 🙏🙏 I…

Four years ago, I wrote an article titled “Minding the ‘gap’,” discussing the CSS `gap` property,…

Adam Wathan has ingeniously developed Tailwind using CSS Cascade Layers, enhancing its ability to organize styles…

Retro techs are no longer stranger things. Just like vinyl records and vintage fashion, retro computing…

Here are some tips to make your content retrieval-ready: Ensure every section can stand on its…

What I believe and why I think SEO content has a packaging problem, is because the…

Blob, Blob, Blob. You either hate them or love them. Personally, as someone not well-versed in…

In an interesting turn of events, Linus Torvalds and Bill Gates meet each other for the…