Similar Posts

5 Tools to Enhance Your AppImage Experience on Linux
The portable AppImage format is quite popular among developers and users alike. It allows you to…
DevSecOps Tutorial for Beginners | with GitHub Actions and Docker Scout
DevSecOps Crash Course | Build a DevSecOps Pipeline with GitHub Actions – SAST Security Scan &…

How To Setup The Hak5 WiFi Pineapple Nano 2024 – InfoSec Pat
Join this channel to get access to perks: https://www.youtube.com/channel/UCYuizWN2ac4L7CZ-WWHZQKw/join Join my discord community to learn and…
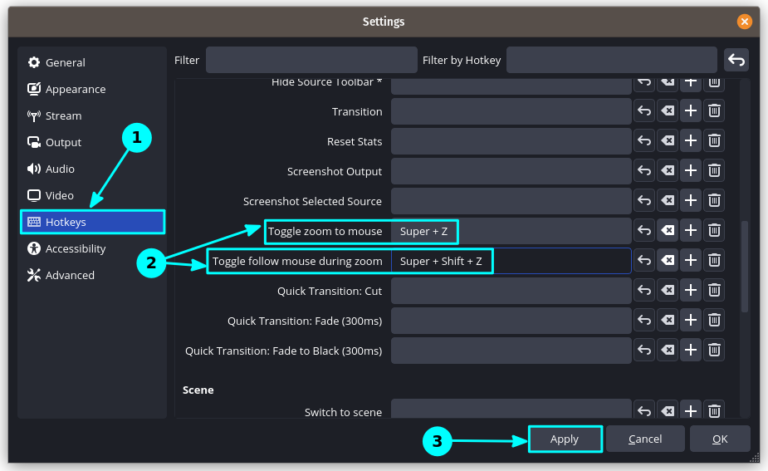
Use Zoom In and Out While Recording in OBS Studio
Have you ever wanted to zoom the screen recording area to where your cursor currently is?…
Build a Touch Slider with HTML, CSS & JavaScript
Build a full screen touch slider with HTML, CSS & JavaScript Full Screen Touch Slider Repo:…