We can’t stress enough the importance of having robust site security. When you’re rushing to meet a deadline, properly securing your WordPress site might not be your biggest priority, so we’ve put together a checklist to make sure you don’t miss any of the essentials.
In a sea of over 2 billion websites, it’s understandable why many people don’t think their site is at risk of being hacked.
And if you’ve never been the victim of an attack, you might not worry about the possibility as much as you probably should.
However, it’s better to have the right protection and not need it, than go without and regret it.
We’ve put together a checklist of 16 steps you might want to take when securing your site – which will hopefully make organizing your security a breeze.
1. Opt For Secure Hosting
2. Mask Your Login URL
3. Use a Password Manager
4. Enable Two-Factor Authentication
5. Use Login Timeouts
6. Set up a WAF
7. Harden Your Security With a Plugin
8. Use Plugins to Carry Out Tasks Automatically
9. Take Steps to Prevent DDoS Attacks
10. Regularly Check for Rogue Accounts
11. Secure Your wp-config File
12. Get Your Site an SSL Certificate
13. Prevent Hotlinking
14. Prevent Spam Comments
15. Visit Your Site Regularly
16. Consider a Static Site
Opt for Secure Hosting
You can take every other step in this article and go above and beyond to harden your site, however, if you’re using cheap, shared hosting, it’s like having a reinforced, ultra-strong, titanium front door – and leaving a key under the doormat.

Without even considering security, shared hosting has enough drawbacks to convince most people to steer clear – but that’s a whole topic in itself. Check out our article on choosing the best type of hosting for your needs for an in-depth look at all of the pros and cons of shared hosting.
Possibly the biggest downside is the lack of security. A vulnerability on someone else’s site could result in the server being compromised and your site coming under attack – through no fault of your own.
Although hosting companies do try and take every precaution to stop malicious attacks like this from spreading, it’s not always possible with shared hosting, as the sites are hosted on the same server.
If you don’t want to worry about what’s going on in your site’s server, opt for VPS or dedicated hosting instead.
WPMU DEV’s hosting gives you dedicated memory, CPU, and SSD storage that is independent of any other sites – including others you host with us!
Top tips:
- Choose a hosting provider that is renowned for having robust security in place.
- Don’t skimp out on the price – spending slightly more on good hosting is better than going cheap and getting hacked.
- Take advantage of features your host offers such as automatic backups, a WAF, or the ability to block suspicious IP addresses.
Secure Your Login Page
Rarely is a hacking attempt personal. You might only run a small website for a boating club in your local village, but that doesn’t mean it will be safe from hackers.
Malicious bots sniff around the internet looking for vulnerabilities in websites and don’t discriminate. If they find that there’s a route past your WordPress login page, they’ll be infecting your files before you can say ”malware!”.
There are a few steps you can take to ensure your login page is safe from these kinds of attacks.
Mask Your Login URL
The first is using a plugin such as Defender to hide your login URL.
This makes it substantially harder for bots to carry out brute force attacks – if they can’t find your login page, there’s nowhere for them to try and crack your password.
It’s super easy to activate within Defender. Just choose a new slug for your login URL.
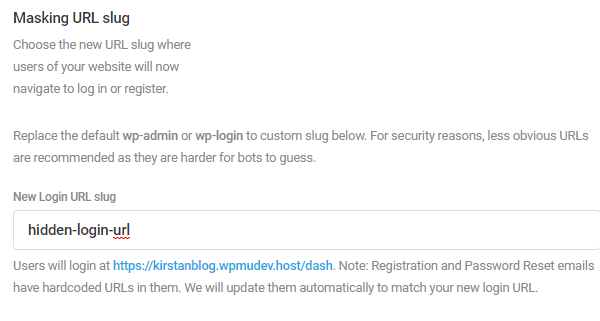
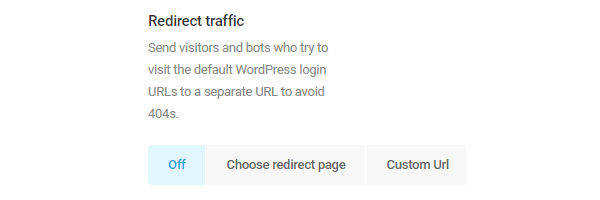
You can also redirect people who try to access your old wp-admin link to a page of your choice.
Use a Password Manager
There are two main rules when it comes to passwords:
- Make sure your passwords are a good length and contain a variety of different characters.
- Don’t use the same password for more than one account.
Adhering to both of these rules can make it almost impossible to remember all of your passwords, which is why you might benefit from a password manager.
LastPass and 1Password are two of the best password managers on the market and will help you create and store complex passwords for all of your accounts.
All you will need to remember is a strong and secure master password – the rest will be taken care of for you.
Enable Two-Factor Authentication
Your password might seem long and complex, however, if a string of 15 characters is all that stands between your data and a cunning hacker, unfortunately, it won’t always be enough.
Two-factor authentication involves linking your phone or another device to your WordPress admin so that it isn’t possible to login without inputting a unique code.
Defender uses Google Authenticator, Microsoft Authenticator, and Authy to do this.
Simply set it for each of your user accounts and each time anyone makes it past the username and password screen, they will be asked to open your authenticator and input the code.

This makes it almost impossible for hackers to get into your site without having access to your username, password AND your mobile device.
To put it into perspective, a site I use purely for testing plugins and themes gets on average 40 login attempts a day by bots. These are bots whose sole job is to try random password combinations with the hope of getting into your site.
All it takes is one of these attempts to be successful and you could lose access to your site completely.
I can see these attempts within Defender’s audit logs.

Even though my site is very obscure and isn’t intended to be public-facing, it’s still on the radar of malicious bots.
And even though my password is secure, I would be a lot more worried if I didn’t have two-factor authentication enabled.
Top tips:
- Using unique passwords for each account can also help you identify the source of an attack if your password is ever compromised.
- Set up a backup email address in case you lose your mobile device and are unable to access your site.
- If you forget your masked login URL, you can retrieve it from your database.
- For extra security, you can remove the password reset link from your login page with a plugin such as Branda.
Login Protection
Defender has some extra tools on his belt when it comes to locking intruders out of your site.
You can set up login protection to ensure that hackers can’t brute force their way into your account by spamming password combinations.
Choose the maximum number of login attempts you want to allow within a certain time frame and display a custom message to anyone outside of the limit.

IP addresses can be banned straight from Defender’s logs. If you see the same IP repeatedly trying to access your site, simply click ‘BAN IP’.

Just make sure (and our Support Team will thank me for saying this) that it isn’t your own IP you are banning, as you will completely lock yourself out of your website!
Defender also offers a few extra ways of managing suspicious IP addresses, which we cover more in this article.
Top tips:
- Add your own IP to the allowlist so you don’t accidentally get hit with a lockout.
- If you are noticing a high number of login attempts from a specific country, you can ban IP addresses from this country altogether using Defender.
- Don’t give your users common names such as Admin or Administrator. Bots will often use these when trying to crack your login details, so if you use a common account name, they’re already halfway there!
Set Up a WAF
A Web Application Firewall (WAF) is a special type of firewall, which sets defined rules in order to help protect a web application from attacks.
All incoming requests and the responses of the web server are examined by a WAF. It monitors, filters, and blocks out unwanted traffic, protecting your site from hackers and other bad traffic.
WAF is simply an intermediary between the web application and the client.
Commonly, a WAF is used against attacks for which traditional solutions do not give protection, such as cross-site scripting and SQL injection, however, it can also be used to protect against illegal resource access – session hijacking for example.
Sound good?
Check out our full rundown of how a WAF works, as well as learn how to take advantage of our awesome WAF (which is included in all of our hosting plans at no additional cost).
Harden Your Site Security With a Plugin
If you want a real chance of preventing any form of attack against your site from being successful, your best bet is with a good all-round security plugin.
Defender has a ton of features that work together to make your site a tough nut to crack.
I could write a full article about all the ways in which Defender can help you secure your site, however – we’ve already done that.
Just to give you a taste, some of its features include:
- Two-factor authentication
- Login masking
- Login lockout
- 404 Detection
- WordPress Security Firewall
- Ability to disable trackbacks and pingbacks
- Core and server update recommendations
- Option to disable file editor
- Ability to hide error reporting
- Update security keys
- Prevent information disclosure
- Prevent PHP execution
Most of Defender’s features are actually free, so head to WordPress.org, hit download, and start deterring those attacks.
Use Plugins to Carry out Tasks Automatically
Fact: computers don’t forget things.
Whether it’s backing up your site or updating your plugins, nothing is as reliable as an automated process.
This is why you should leave these tasks to the experts – a couple of awesome WordPress plugins!
Updating with Automate
Hackers love finding vulnerabilities in plugins and themes and using those as a way to infiltrate your site.
When a developer is made aware of a potential exploit in their product, they will create a patch that will fix the vulnerability.
If you neglect to update your plugins and themes when new patches are released, you could be leaving the holes open for hackers to walk in through.
This is why it is important to make sure updates are applied as soon as they are released, and is where Automate comes in.
When you run a number of WordPress sites, it can be time-consuming to update all of the plugins and themes manually, meaning sometimes this task can be put on the backburner.
Automate automatically detects when your website is running out-of-date plugins, themes, or an outdated version of WordPress, and automatically updates your website to run the latest versions.
Better yet, it can even take a backup of your site before it installs the updates, just in case there is a compatibility issue that causes problems.
Check out our docs for a full tutorial on how to set up Automate.
Backup with Snapshot
The plan, of course, is to avoid getting hacked.
However, if the worst does happen, having a backup of your site can save the day.
There is no better way to do this (in my humble opinion!) than with a reliable backup plugin like Snapshot.
Simply choose how often and at what time you want your backups to take place, and you’re all set.

This article will give you a full rundown on how to set up and manage your backups with Snapshot.
Top tips:
- As well as updating your plugins and themes regularly, make sure you keep an eye out for new versions of PHP and SQL which should also be updated as soon as possible after release.
- It’s always good to take period manual backups and save them locally too – you can never be too safe when it comes to site security!
Protecting Against DDoS Attacks
A Distributed Denial of Service (DDoS) attack is when a website is flooded with traffic in order to cause disruption to its service.
It is carried out by a network of computers (sometimes computers of oblivious members of the public who have been infected with malware). The attacker uses these devices to form a ‘botnet’, which they can instruct to attack a particular target.
The purpose of these attacks is often to hold the site owners to ransom, and there have been some high-publicity cases of DDoS attacks in the past. Some are carried out simply for fun and to cause chaos, but whatever the reason behind the attack, being a victim of one is never ideal.
Luckily, there are some steps you can take to prevent it from happening to your site.
These include:
- Disabling XML-RPC
- Using a firewall
- Disabling trackbacks and pingbacks
- Disabling Rest API
- Using a CDN.
These steps are all covered in detail in our DDoS attack prevention guide.
Regularly Check for Rogue Accounts
When you’re working in WordPress often and are used to flicking between the same few screens, it’s easy for certain things to slip through the net.
This is why you need to make time to manually check that no one else has access to your site.
Something you should be regularly checking for is rogue accounts.
This applies to not just additional WordPress users, but also FTP and SSH accounts.
If you host with WPMU DEV, this info is available within The Hub.

Secure Your WP-Config File
Your wp-config holds the keys to your entire WordPress site and is the last thing you want hackers to get their hands on.
One way to ensure it’s out of reach is by moving it out of your web-root folder.
Take a look at WordPress’ own advice regarding this to decide whether it’s the right route for you.
If you don’t want to move it completely, you can block access to it by adding the following code into your .htaccess file.
<files wp-config.php> order allow, deny deny from all </files>
Top Tips:
- Take it one step further by blocking access to your .htaccess too!
Get Your Site An SSL Certificate
An SSL certificate verifies that the website you have arrived at is the intended destination, by checking the credentials of its certificate.
This helps prevent domain spoofing and other similar attacks.
A connection that involves an SSL certificate is more trustworthy, secure, and gives a much better impression to the customer.
This is because an SSL certificate turns an HTTP connection into an HTTPS connection – the added ‘S’ literally stands for secure.

You can obtain an SSL certificate through a trusted provider such as Let’s Encrypt.
Top tips:
- If you’re running a multisite network, check out our free wildcard SSL.
Prevent Hotlinking
If someone is hotlinking your pictures, they are using the link to your original image on your site, which means that their visitors are getting the benefit of the image, but your server is picking up the tab.
Not only is it considered unethical, but this can put a lot of strain on your server, causing issues for your site, and could also result in extra costs.
There are a number of ways to secure your images, one of the easiest being to add a code snippet to your .htaccess file.
This code will ensure that only certain websites are allowed to display your images. You can specify the individual sites.
RewriteEngine on RewriteCond %{HTTP_REFERER} !^$ RewriteCond %{HTTP_REFERER} !^http(s)?://(www.)?example.com [NC] RewriteCond %{HTTP_REFERER} !^http(s)?://(www.)?google.com [NC] RewriteCond %{HTTP_REFERER} !^http(s)?://(www.)?youtube.com [NC] RewriteRule .(jpg|jpeg|png|gif)$ - [F]
This is the code needed for sites running on Apache servers.
location ~ .(gif|png|jpeg|jpg|svg)$ { valid_referers none blocked ~.google. ~.bing. ~.yahoo. yourdomain.com *.yourdomain.com; if ($invalid_referer) { return 403; } }
Use this code if your site is running on an NGINX server.
Top Tips:
- You can also protect your images using a plugin or a CDN with hotlink protection.
- Add a copyright notice to your theme’s footer to discourage people from even trying to steal your images.
Stop the Spam
Spam comments on your blog are not just frustrating – they can pose a security risk, too.
Many spam comments contain malicious links in the hope of tricking your visitors into submitting their personal information.
So, although you might not be the intended target of these kinds of attacks, you have a duty to the visitors of your site to keep them safe.
If you’re getting hit with a tonne of spam, you have two options: turn off your comments altogether, or install an anti-spam plugin.
If you choose the latter option, Akismet may be just what you need.
Each comment left on your site, PLUS your form submissions are all run through their global database of spam to prevent malicious content from making its way onto your site.
It’s free – and it works!
Visit Your Site Regularly
Sometimes the simplest solution can work wonders.
If your site has been hacked and your content has been meddled with, a quick glance at your site should tell you that in seconds.
Visiting your site and seeing it from a customer’s point of view is good not just from a security perspective, but from accessibility and aesthetic angles too.
So get yourself a coffee, take a seat, and browse your site as though you’re a regular visitor.
Top Tips:
- Don’t forget to view your site whilst logged in, logged out, and in incognito, too!
Consider a Static Site
If you run a site that requires little user input, i.e. is mostly for sharing information, rather than an eCommerce store or a busy blog, converting to a static site might be beneficial.
To do this, you need to create copies of your files and bundle them into a neat .ZIP which can be stored on your server.
This means that your actual WordPress installation can be safely hidden away and out of reach to bots and hackers.
It’s not the right route for a lot of sites, but feel free to check out services such as Strattic or Simply Static if you want to research it further.
Better Safe Than Sorry
We know that implementing so many different steps can seem like a tedious job, but luckily, once you’ve ticked most of these off your list, they will look after themselves.
Plugins run quietly in the background and do the hard work for you, so once you’ve set up all your security for your new site, it shouldn’t require much ongoing manual input.
When you have other aspects of the site to worry about, security might get pushed to the backburner, however…hindsight is a wonderful thing.
Make the time now to implement the right security procedures for your site and hopefully you’ll never have to deal with the frustration of your site being hacked and wishing you’d taken precautions sooner.
Source: premium.wpmudev.org