
When you start exploring a target website, the first question to ask is simple: what names exist out there?
Before you think about vulnerabilities or exploits, you would want a map of subdomains. That map can reveal forgotten login pages, staging servers, or even entire apps that weren’t meant to be public.
My preferred tool for this first step is subfinder. It’s simple, quiet, and quick. In this guide, we’ll walk through installing subfinder on Kali Linux, running the most useful commands, saving results, and experimenting with extra flags.
We’ll practice together on vulnweb.com, a safe site for learning.
What subfinder actually does
Subfinder is a passive subdomain discovery tool. Instead of hammering DNS servers or brute-forcing names, it asks public sources: certificate transparency logs, DNS databases, GitHub, and more. That’s why it’s fast and low-noise.
The catch: subfinder gives us names only. Some names may be stale and some may point to nothing. And that’s fine. At this stage, all we need is a clean list of possible subdomains. Later, we can resolve and probe them.
Installing subfinder on Kali Linux
You have two easy choices:
Install via apt (fastest):
sudo apt update
sudo apt install subfinder
Install the latest version via Go:
go install github.com/projectdiscovery/subfinder/v2/cmd/subfinder@latest
echo 'export PATH=$PATH:$HOME/go/bin' >> ~/.bashrc && source ~/.bashrc
If youn are just starting out, the apt version is fine. If something feels buggy, you can switch to the Go install for the newest release.
Understanding the basic flags
-dchooses the domain-silentprints one subdomain per line, no banners-osaves to a text file-oJsaves JSONL (structured data, one object per line)-lsshows which sources subfinder can query-sselects only certain sources-alluses every available source
Using subfinder
Subfinder has more options that are useful once you’re comfortable with the basics. Let’s walk through them with examples:
Enumerate subdomains (basic):
subfinder -d vulnweb.com
Here’s what will happen next:
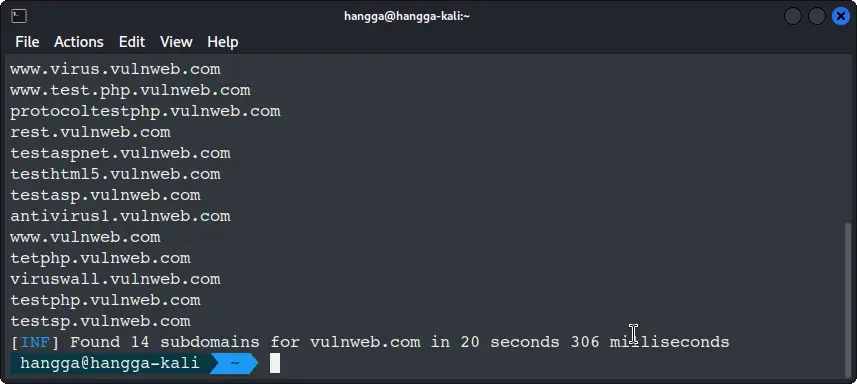
Awesome, all the subdomains are now visible.
Enumerate multiple domains from file:
Runs against every domain listed in domains.txt.
subfinder -dL domains.txt
Use all sources:
Queries every source subfinder knows about. Slower, but more complete.
subfinder -d vulnweb.com -all
Exclude specific sources:
subfinder -d vulnweb.com -es alienvault,zoomeyeapi
Skips certain sources if you don’t want to use them.
Set concurrency (threads):
subfinder -d vulnweb.com -o results.txt -t 50
Runs with up to 50 concurrent tasks.
Limit request rate:
subfinder -d vulnweb.com -rl 50
Keeps requests under 50 per second.
Output to a plain file:
subfinder -d vulnweb.com -o results.txt
JSON output:
subfinder -d vulnweb.com -oJ vulnweb.jsonl
CSV output (via quick conversion):
subfinder -d vulnweb.com -oJ subfinder.jsonl
jq -r '.name' subfinder.jsonl | awk 'BEGIN{print "subdomain"}{print $0}' > subfinder.csv

The output has been saved to subfinder.csv. Open it to view the data.
Unique results only:
subfinder -d vulnweb.com -silent -o results.txt
sort -u results.txt > results_unique.txt
Recursive enumeration (find deeper subdomains):
subfinder -d vulnweb.com -recursive
Provider configuration (optional but powerful)
You can add API keys of premium services like SecurityTrails, Shodan etc. They will give you richer results. You can add keys to ~/.config/subfinder/provider-config.yaml:
securitytrails:
key: "YOUR_SECURITYTRAILS_API_KEY"
virustotal:
key: "YOUR_VIRUSTOTAL_API_KEY"
shodan:
key: "YOUR_SHODAN_API_KEY"
You can use subfinder without keys, but adding them usually gives us more coverage.
Simple practice exercise with vulnweb.com
Let’s get into practice mode and run a few simple coommands to explore subfinder:
Collect subdomains:
subfinder -d vulnweb.com -silent -o vulnweb_raw.txt

Clean up duplicates:
sort -u vulnweb_raw.txt > vulnweb_clean.txt
The following command will create vulnweb_clean.txt with unique entries:

Done! The cleaned list is in vulnweb_clean.txt — go check it out.
Next, save JSON output too (for reports):
subfinder -d vulnweb.com -oJ vulnweb.jsonl

Take a look at the first 10 results:
head -n 10 vulnweb_clean.txt

Now you have a tidy list of candidate subdomains, ready for the next step of vulnerability assessment.
Final notes
Subfinder is the quiet scout in the toolkit. It doesn’t overwhelm us with noise, it just hands out the names that exist out in the wild. With a few simple commands, we can build a reliable subdomain list for any domain we’re testing.
For now, practice on vulnweb.com until you’re comfortable. Later, move on to checking which of those names are live and what services they’re running. But that’s another story for another day.