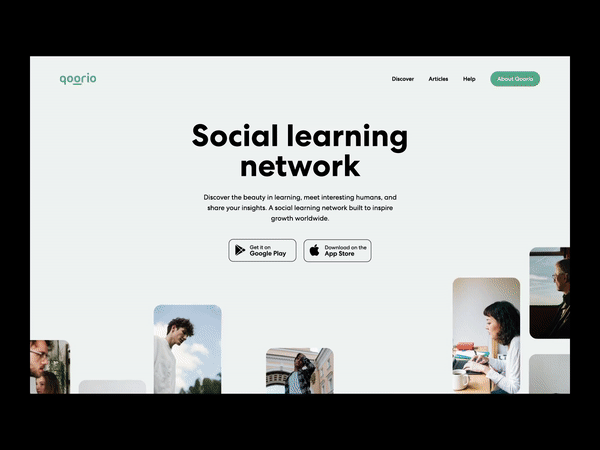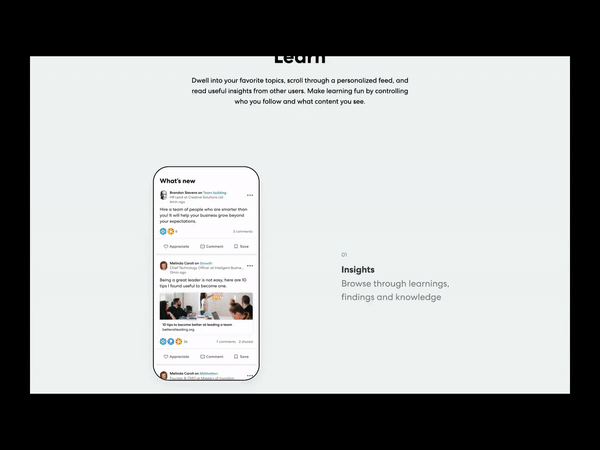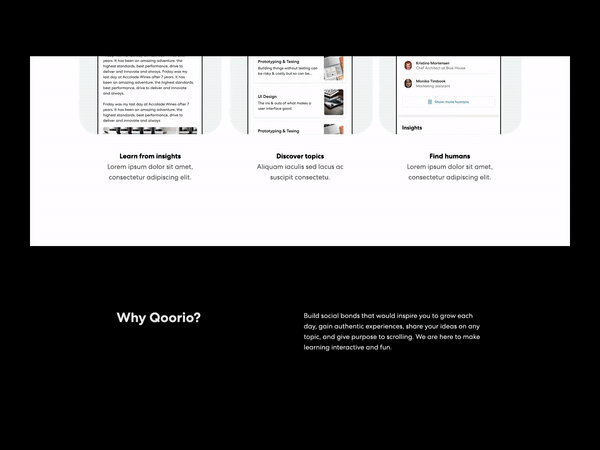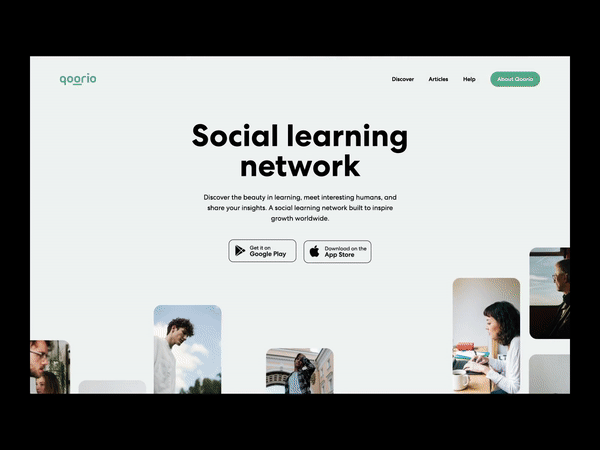
25 YouTube stats and facts to power your 2021 marketing strategy
If you’re interested in ramping up your video marketing strategy in 2021, you’re probably doing some research into the best platforms to use. If you’re trying to figure out how YouTube fits into your approach, we have a list of 27 must-know YouTube statistics to help you understand how the platform is being used right now.…
Read More